Statistically, there’s almost a one in three chance (29.6%) that your business will experience a data breach in the next two years, according to a 2019 study by IBM and the Ponemon Institute. Your company might even be getting hacked as you read this because of almost two-thirds experience attacks on a weekly basis.
However, IBM’s 2020 study found that teams that had a tested incident response plan (and a team to run it) saved an average of $2M (51.8% savings on the cost of an average data breach) compared with those that didn’t.
So although prevention is an essential part of your cybersecurity efforts, the way you respond following a breach is just as important with regard to how it impacts your organization.
The right way to respond after a breach has occurred is different in every case (it depends highly on what type of data was taken, how the breach occurred, and more). But there are a number of strategic best practices to follow that will help you limit the impact on your business.
Here are four critical high-level steps that your response should include.
1. Consult With Legal Counsel
Most states/countries have legislation around security breaches involving personal information (in various levels of comprehensiveness and completeness). And you’ll need to follow them after a breach; otherwise, you could face severe consequences.
The General Data Protection Regulation (GDPR) is a great example of legislation that has severe penalties for not following its requirements. In the event of a breach, you’re required to notify your users within 72 hrs; if you fail to do so, you could see fines as high as €20M or 4% of the previous year’s annual revenue.
However, the legal ramifications of a breach are often hard to assess in some countries (the United States, for instance) because their data protection laws are fragmented and inconsistent. So it’s worth considering independent legal counsel with data privacy expertise to ensure that you’re doing everything that’s required.
Bottom line, your legal requirements will affect everything you do next. So start here to ensure you have an accurate picture of your obligations.
2. Secure Your Data and Systems
After a breach, you need to secure your systems and limit further data loss right away. It could save you an average of $164,386, according to IBM’s 2020 study. However, you’ll want to ensure that you do it the right way — you don’t want to obstruct a criminal investigation. Here are the best practices you’ll want to follow.
Determine The Scope of The Breach
First things first: Determine the entire scope of the breach. Otherwise, you may miss something and fail to completely stop it.
To determine the scope of a breach, assemble a team of experts (your Incident Response (IR) team) who are capable of determining the following:
- What was accessed? Which parts of your systems were affected, and what data did it contain?
- How was it accessed? What were the vulnerabilities that allowed unauthorized access?
- What (if anything) was taken? Not all breaches result in stolen data, but you’ll need to determine if anything was stolen because it determines the steps you’ll need to take next.
- Is your data available to the public on the internet? If you’re unsure, start searching right away to determine if it is.
The best people for your IR team will depend on the breach. But they could include your legal counsel, IT team, cybersecurity team, HR team, communications team, and more. Consider hiring an independent forensics team to help you collect evidence because some of the actions you take to stop a breach may affect an investigation.
Ideally, you should have your IR team predetermined and trained to assess the scope of any breach before one occurs. It’s one of the most effective ways to limit the effects of a breach on your business.
Secure Relevant Equipment
As you determine the scope of the breach, immediately take any affected equipment (servers, computers, etc.) offline, and secure related physical locations associated with them. This will prevent any further unauthorized access.
However, be sure to leave that equipment turned on until forensics has a chance to look at it. Otherwise, it may obscure the collection of important evidence (like traces of malware, etc.).
Additionally, update the login credentials of people who have authorized access to the systems/physical locations that were breached, regardless of whether that was the cause. Compromised credentials are the cause of over 19% of all breaches, and this extra step ensures that you won’t receive another attack on the same data this way.
Remove Breached Data From The Internet (If Possible)
The faster you remove any breached data from the internet, the less impact it will have on your users. So if yours is posted somewhere (the dark web, for instance), take steps to remove it immediately by contacting the site and requesting that they take it down and delete it from their archives.
Keep in mind that some search engines also store your data in a cache for a certain period of time. Don’t forget to contact them and make sure they haven’t archived it mistakenly.
3. Notify Relevant Parties
Legally speaking, if you don’t notify the right people at the right time about a breach, you could be slapped with a significant fine (like the $35M fine the SEC hit Yahoo with for failing to notify investors for almost two years).
However, notification is more than just a legal issue — it’s also about maintaining the trust (and business) of your customers. Failing to notify your users of a breach is a very bad move, from a PR perspective, as Uber learned in 2018.
Determine Your Legal Obligations
Many countries have specific requirements in their data privacy legislation that dictate whether, when, and how you should notify those affected by a security breach.
Unfortunately, there’s no one-size-fits-all best practice here: You must check the specific laws or regulations as they pertain to your business. Keep in mind that the type of information leaked in the breach might have special legal requirements as well (for example, medical data).
Here are a few links to resources that can help determine your requirements:
- U.S. Data Breach Notification Laws by State: A complete breakdown of U.S. data protection and notification requirements for every state
- GDPR: European data privacy laws and notification requirements
- HIPAA: Medical specific data protection and notification requirements per the U.S. Department of Health and Human Services
Notify Law Enforcement
Law enforcement officials can help you navigate the aftermath of a breach, so you’ll want to get them involved early in the process to help you with your investigation. The right law enforcement to notify will vary depending on where you’re located and what laws your business is subject to. Check with your legal counsel on who you need to contact.
Additionally, make sure the law enforcement you’re working with is experienced in dealing with cybercrimes. If your local police department isn’t equipped for the task, you may need to escalate it to one that is.
Notify Users
The sooner you notify your users, the better they’ll be able to protect themselves from damages associated with the breach. For example, if their credit card numbers were stolen, they can call their provider and lock their cards to prevent unauthorized purchases.
Or, if their Social Security numbers were taken, users can take steps to reduce the effects of identity theft right away — for example, by contacting a credit bureau and implementing a credit freeze.
Most countries/states have specific laws about how to notify your users if they are affected by a breach. So follow any legal requirements to the letter. However, for the sake of trust and transparency, you’ll generally want to share the following information with anyone who was affected:
- How the breach happened
- What information was taken, and how it affects your users
- How cybercriminals have used that information (if you know)
- What you’ve done to correct the situation
- What you’re doing to help your users with any negative consequences they may experience as a result of the breach (credit monitoring, for instance)
- How to get in touch with questions about the breach
As Target proved with the way they handled their 2013 data breach, consumers value transparency when their personal data is exposed. So while you will experience a loss of trust, being upfront about it and controlling the narrative will help you retain some of that trust that you might not otherwise.
4. Correct Vulnerabilities to Prevent Future Breaches
Once the immediate threat of your latest cyberattack has passed, it doesn’t mean it’s OK to cross your fingers and hope that the rest of the security systems you have in place will do their jobs. It means it’s time to audit and address other vulnerabilities in your systems right away to prevent another incident and limit the further impact to the business.
The loss of trust from a breach is extensive. Studies show that anywhere from 65% to 80% of your customers will lose faith in a breached company. The impact? Millions in lost business, according to IBM/Ponemon:
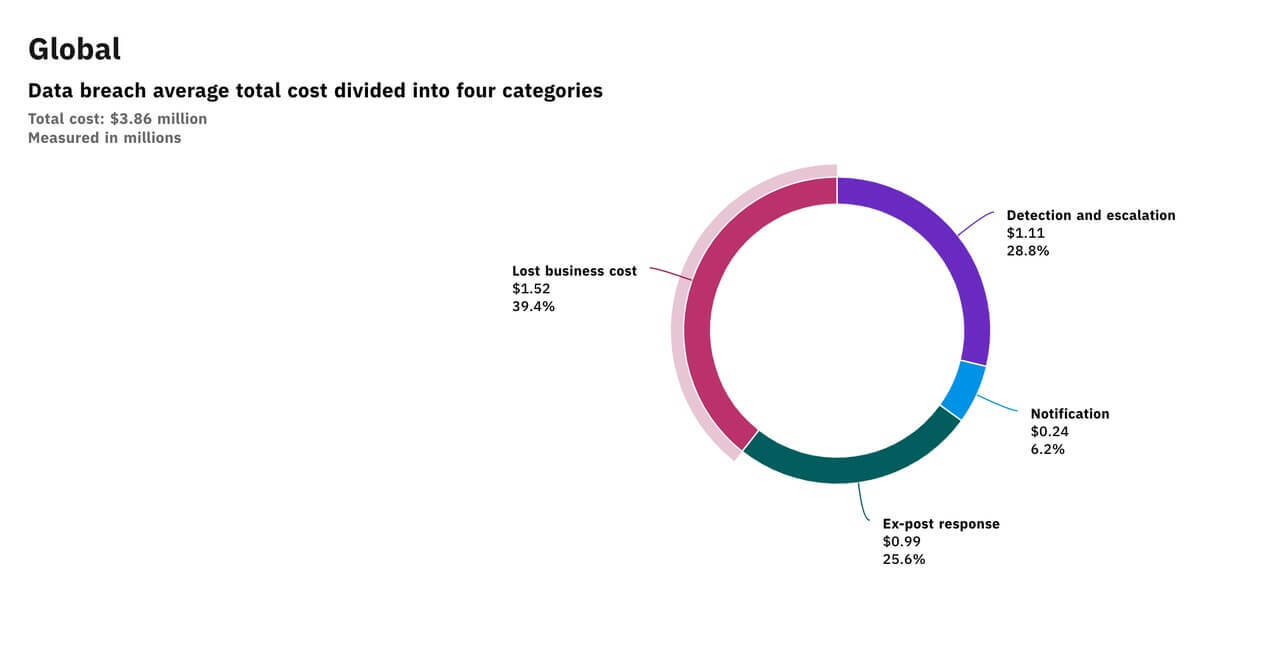
Courtesy of IBM/Ponemon Institute
Simply put, another data leak could be devastating for your business. So here’s what we recommend doing to strengthen your information security in the wake of a breach.
Audit and Reduce Access to Critical Data
Internal human error is a major cause of data security incidents, which means that as more people within your organization gain access to data, your risk for an incident skyrockets:
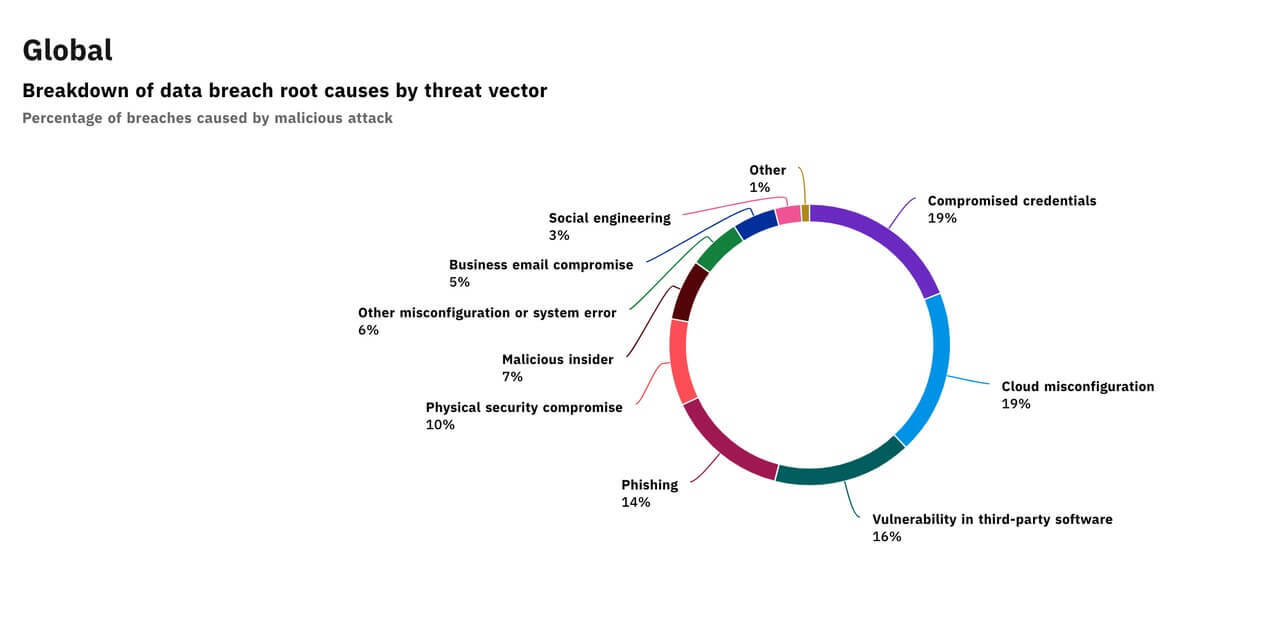
Courtesy of IBM/Ponemon Institute
That’s why Verizon consultants who assessed the aftermath of Target’s epic data breach recommended reducing access to critical data as an important step forward for the retailer, which was outlined in their report:
“Target should limit the access to portions of the network containing business-critical systems to only the employees who directly manage those systems. Where possible, Verizon recommends restricting employee network access based on job function.”
Bottom line, one of the best things you can do following a breach is audit who has access to sensitive information and limit it to essential personnel only. The fewer people who have access to important data, the less likely something is to go wrong.
Encrypt Everything
Robust data encryption will make your data useless to hackers (even if it’s breached) because most don’t have the mathematical muscle or the patience to decrypt it.
Unfortunately, it’s taken quite a while for companies (even major ones with extremely sensitive data) to follow through — and they’ve paid the price.
For example, In 2014, hackers stole millions of customer records (all unencrypted) from Anthem, the second-largest health insurer in the United States. And although you’d think that would be a wake-up call for other companies, unencrypted records for over 140 million people were stolen from Equifax three years later.
Given the constant barrage of cyberattacks that have a proven track record of breaking into the most advanced security systems, every company should be encrypting their data, no matter what. Here are three ways to encrypt yours:
- Data encryption converts information into another form, kind of like a secret code. The only way to read the data is to decipher it with a unique key. Modern encryption uses algorithms that make it extremely hard to crack.
- Tokenization replaces your data with unique symbols that retain all the information without compromising it. When the token is processed through the right tokenization system, it reveals the actual data.
- Data de-identification separates personal identifiers, such as name or Social Security number, with its related data, making it hard for hackers to figure out which data belongs to which individual.
Improve Authentication Security
Compromised credentials are one of the two largest causes of all data breaches, according to IBM and the Ponemon Institute. So taking steps to improve the security of your authentication process following a breach is essential to ensuring one does not occur this way in the future.
Here are two easy ways to improve authentication security:
- Breached Password Detection: Breached password detection checks users’ credentials against a database of breached credentials in real-time (that is, right when they log in). It will notify them if their password is breached, and you can even prevent access until the user has reset their password.
- Multi-Factor Authentication: Multi-factor authentication requires users to confirm their identity in two or more ways in order to log in. This prevents unauthorized access, even if their credentials are compromised.
Hack Yourself to Anticipate Future Attacks
If you are going to get hacked, it’s better (and cheaper) to pay someone to do it intentionally first. You’ll tighten up your systems, and your team will be more prepared if the real thing happens.
This approach is also better than an automated scanner because penetration testers actually attack your network and exploit your system’s weak points, as a real hacker would. The goal is to test the real-world effectiveness of your security system against savvy human hackers, who will try everything in the hacker playbook to break in. And you can’t replicate that with an automated system (yet).
Major tech companies, including Google, Facebook, and Microsoft, are already doing this and have taken penetration testing a step further by creating bug bounty programs. These programs challenge independent “pink hat” hackers to find vulnerabilities or other bugs that affect the security of their systems. And Google paid out over $6.5 million in 2019 alone to those who found gaps in their networks.
Strengthen Your Weakest Link: Humans
Humans are by far the weakest link in your cybersecurity efforts. Phishing scams, ransomware, and weak passwords lead to almost 50% of data breaches.
Plus, now that more people are working remotely in the wake of COVID-19, employees are also taking their work outside the office, using several portable devices that contain sensitive data (which opens up more opportunities for theft and unsanctioned devices lacking proper encryption).
So effective cybersecurity in 2020 is a lot more than just 1s and 0s — it’s a culture.
Studies show that strong ownership at the employee level improves cybersecurity and reduces the number of incidents an organization experiences. And training (plus the right tools) can help you encourage it:
- Educate employees with comprehensive and constant security training. Whether it’s handling data or recognizing spam emails/social engineering practices, employees need to know how to identify and address security issues. Training is the most important security measure you implement to combat these attacks.
- Give employees the tools to better secure their devices. Implementing multi-factor authentication adds another layer of security on your employees’ devices. This eliminates the concern of an employee losing a device or inadvertently sharing their password. Even if their password is stolen, the account can’t be accessed without the second factor, like a physical device or a biological feature, such as a fingerprint.
- Improve user experience. A seamless user experience that supports proven security practices and encourages secure behaviors is essential to building a strong cybersecurity culture. Avoid complexity at all costs.
Above all else, the key to creating a cybersecurity culture is showing your employees why it matters. Policy alone won’t encourage them to care — you have to help them see what’s at stake. Their vigilance could prevent the next breach altogether.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.