Ah, Valentine's Day! Love is in the cloud. Billions of people are either signing up for or logging in to web services to wish their loved ones a happy day. They are ordering flowers, buying chocolates, or sharing the most intimate of thoughts through messages. Building scalable authentication the right way to sustain spikes in demand can leave developers with a heavy heart.
However, Auth0 can help you prepare for the best and the worst today and every day. Let me show you why using Auth0 can make you fall in love with authentication through these solid Auth0 features that make modern authentication a walk in the park.
Single Sign-On Will Keep Us Together
According to the 2018 World Password Survey run by MacAfee, consumers who responded to the survey have an average of 23 online accounts that require a password but on average only use 13 unique passwords for those accounts. With so many passwords to track, forgetting a password is common.
Going through the motions of resetting a password can bring some heartache... Imagine if one of the "Challenge Questions" is asking you about the favorite vegetable of your ex. However, not being able to recover the account or getting it compromised can truly unleash the worst of heartbreaks.
This all could be alleviated if we only needed to remember one username and one password, right? Find the one and be forever happy with easy access to all of our accounts. This sounds like a fairy tale but it's not. Fortunately for us, Password Charming exists in the form of Single Sign-On.
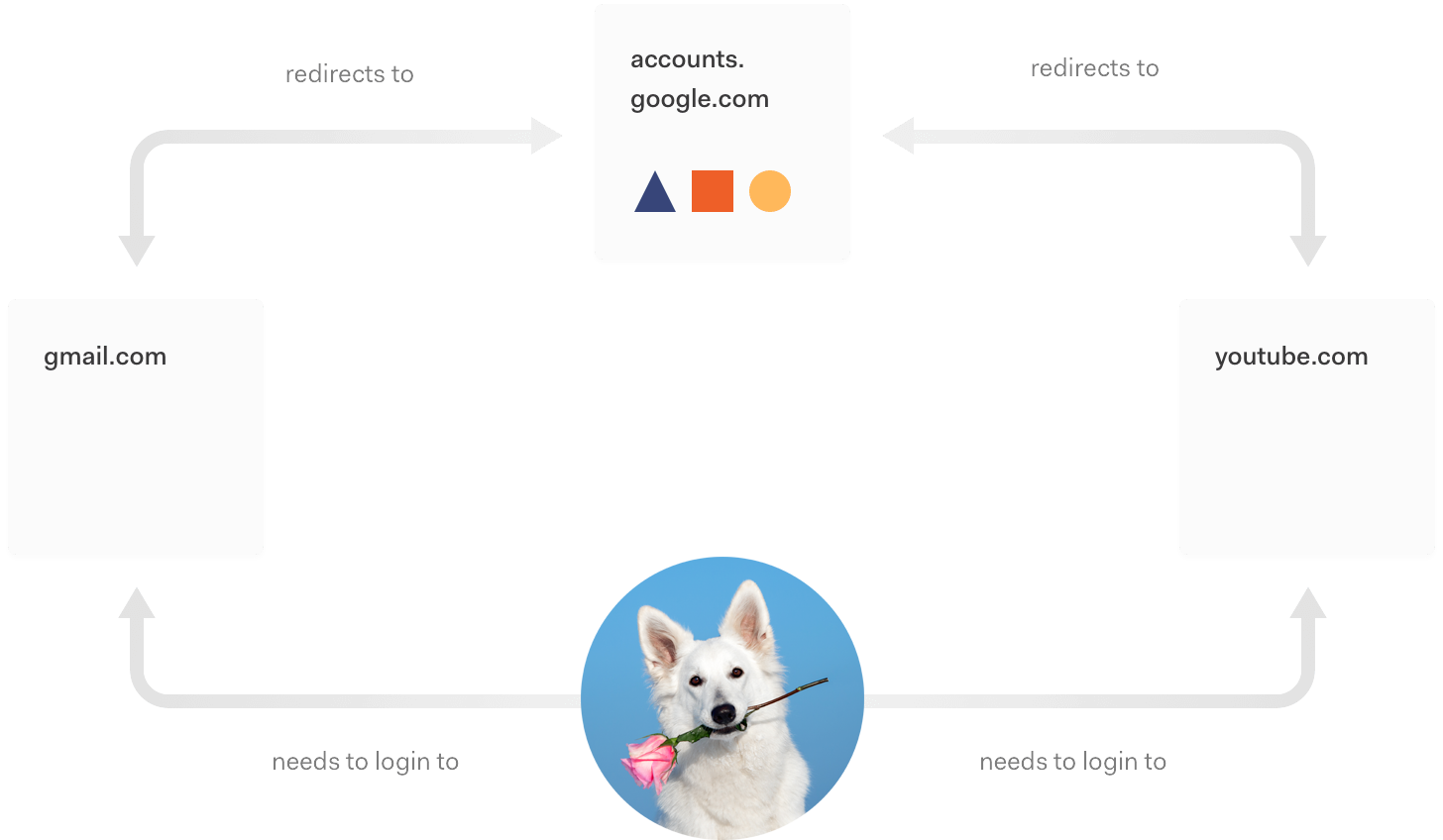
Single sign-on (SSO) allows users to simply log in once and use all applications they have been granted access to. You could use your Google account to authenticate yourself with a dating site or any other application that decided to delegate the responsibility to create, maintain, and protect your username and password to Google.
Building and maintaining an identity platform with Single Sign-On can become expensive, time-consuming, and difficult to get right — just like love. In a recent survey, 94% of organizations said they were able to implement Auth0 in less than a month. That is possible because with Auth0’s SSO solution you get:
- Over 40 supported Identity Providers including mainstream social providers such as MySpace. Kidding!
The ability to authenticate the social butterfly by consolidating duplicate accounts across various providers with account linking — while increasing conversion rates.
Ease of use by having the freedom to write your code once and integrate any configured connection. One login screen to rule them all.
Like meeting the expectations of even the strictest of parents, compliance with leading organizations including SOC2, GDPR, HIPAA, and others.
Let Auth0 help you get SSO right today to help your customers fall in love with an amazing authentication user experience. Don't let any customer be the one that got away because he or she forgot to remember you.
Rules to Love
Relationship needs are not static. They change as the relationship grows... or dwindles. Authentication is one of the most critical relationships you'll ever form with your customers. This process helps you understand who they are and how you can help them based on an established and ongoing relationship around identity. Therefore, authentication needs to be extensible, flexible, and customizable.
With Auth0 Rules, you can customize your authentication workflow. Auth0 Rules are JavaScript functions that execute when a user authenticates to your application. They run once the authentication process is complete. You can use them to customize and extend Auth0's capabilities.
Use Auth0 Rules to:
Enrich user profiles: query for information on the user from a database/API, and add it to the user profile object.
Create authorization rules based on complex logic (anything that can be written in JavaScript).
Reuse information from existing databases or APIs for migration scenarios.
Keep a white-list of users and deny access based on email.
Notify other systems through an API when a login happens in real-time.
Modify tokens: Change the returned scopes of the Access Token and/or add claims to it, and to the ID Token.
Let Auth0 help you rule the authentication game today.
Universal Login: One Form, One Heart
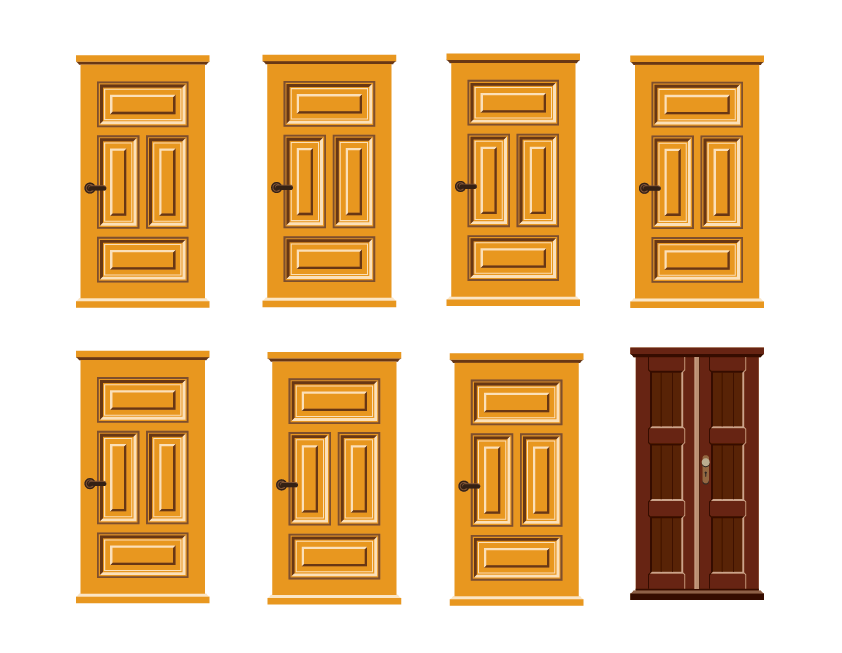
One of the easiest ways to improve your customers’ experience while boosting security is through consistency. Imagine that each login form in your application is a physical door. If the look and feel of this door are not consistent throughout the application, your customers' user experience when logging in may look like this:
Each door that represents a login form looks different. They are all valid entryways for the customer's credentials, but your customer can't anticipate what the login form should look like. This inconsistency can let a malicious actor to phish your customers. Here’s how:
The attacker creates a site and requests your customers' login. If your login forms are inconsistently designed, for your customers, the brown door may just signal a new form design. They could easily enter their credentials there expecting access to your application — and just like that, they become phishing victims.
To help protect your customers, a consistent authentication UX and UI helps them better identify when a phishing attempt may be happening. Say that you opt for all of your login forms to look like the yellow door. Now it's much harder to trick one of your customers:
The universal design and implementation of the login makes your customers expect one, and only one, form for their credentials. Anything different must be rejected.
Auth0 offers you an easy way to build this unique door for your customers through Universal Login. Anytime your customers need to log in, they are redirected to a central authorization server that presents them with a login form that embraces your brand. Since authentication takes place on the same domain as the login, credentials are not sent across origins, increasing security and protecting against phishing and bucket brigade attacks, also known as man-in-the-middle (MITM) attacks.
Universal Login and SSO also happen to be a match made in heaven. You can orchestrate single sign-on (SSO) between multiple apps. If the user has already signed on to one app, the login page will not be shown again and the user will be logged in via SSO.
Play this video to see it in practice!
Love and security are based on trust. Don't let phishing steal your customers' trust in your design or implementation. You can get started with Universal Login from Auth0 today.
Multi-Factor Authentication: Are You the One for Me??
Left image source: Gage Skidmore
Pictured above are two different and unique women. One of them is Jaime Pressly and the other one is Margot Robbie. If someone gives you the picture of one of them and tells you to hand her a super secret script for an upcoming Spider-Woman movie, would you be able to tell them apart?
It would be very difficult. Even if you were to ask one of them for their name... What if Margot, jokingly, says her name is Jaime. You need to ask more questions to establish their identity and not make the mistake of giving the prized script to the unintended person.
Authenticating users is just like that. If you want to have greater confidence that you are granting data access to the right person, multi-factor authentication is for you.
Multi-factor authentication (MFA) is a method of verifying a user's identity by requiring them to present more than one piece of identifying information. This effectively provides an additional layer of security, decreasing the likelihood of unauthorized access. The type of information required from the user is typically two or more of the following:
- Knowledge: Something the user knows (such as a password)
- Possession: Something the user has (such as a mobile device)
- Inheritance: Something the user is (such as a fingerprint or retina scan)
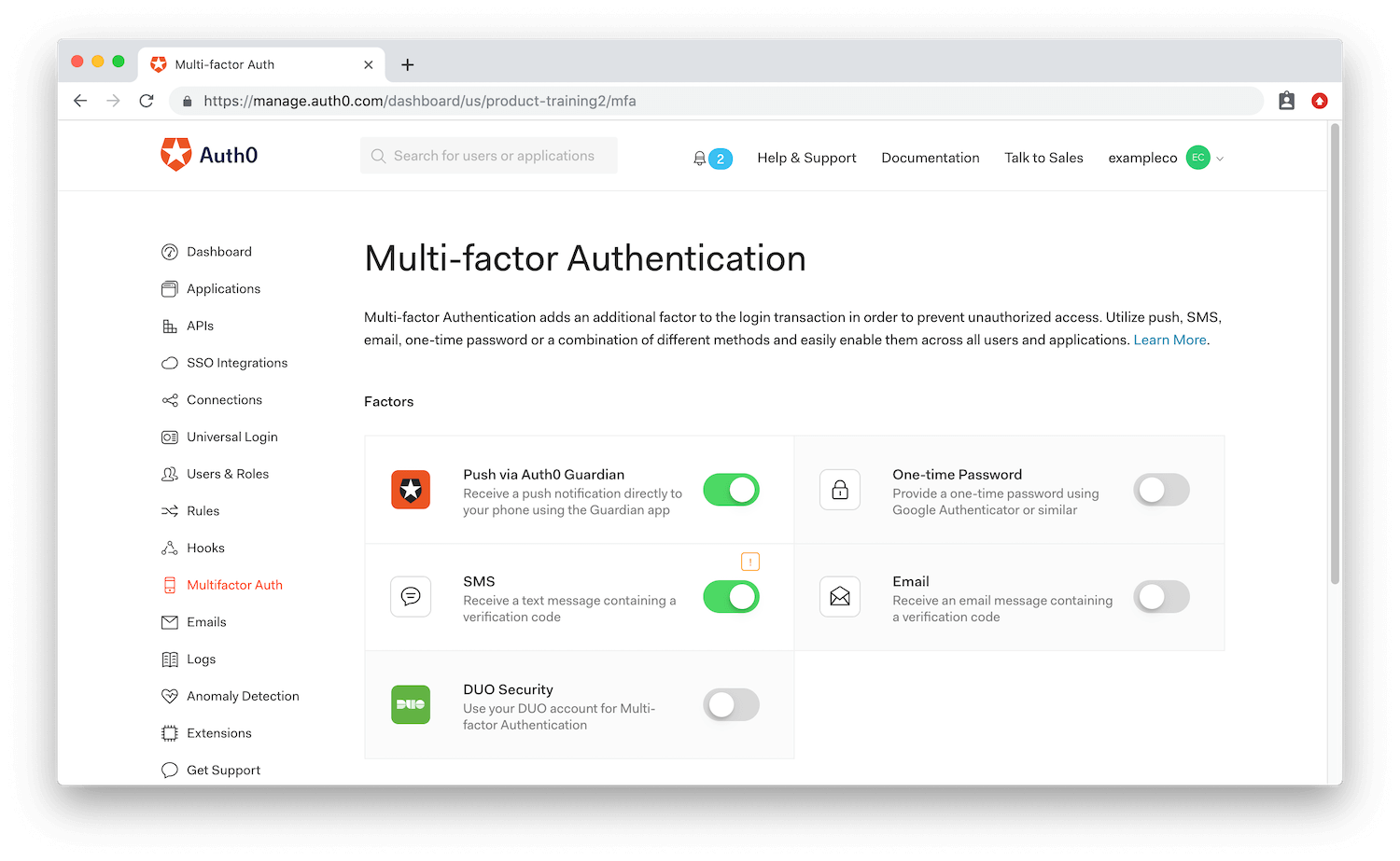
The complexity of getting MFA right keeps developers from implementing it in their applications. However, with Auth0, enabling MFA for your application is a fairly straightforward process:
Choose what factors to enable on your application, such as push notification.
Perform any further setup required to configure that factor.
Choose whether or not you wish to enforce MFA for all users.
With Auth0 Rules, as you learned earlier, your application's MFA experience can be customized. You can only require MFA in specific circumstances or force a particular factor to be used. When in doubt, always ask: is he or she the one to log in?
Catfishing? Ain't nobody got time for that! Don't let doubt erode your confidence and increase your risk of leaking data. Love, trust but verify. Give Auth0 Multi-factor Authentication a try today.
Anomaly Detection: Trouble in Paradise
You know that I trust you, baby
But your data's so good lookin'
I'm afraid somebody's gonna steal it away from me.
We know that most of the time it's your customers who are authenticating into your application, but we also know that their data is beautiful and attractive to many malicious users out there. They will try to pretend to be your customer by deception or by force.
Legitimate users may try to log in three or five times if they have forgotten their password but are trying to remember it:
Was it
correcthorsebatterystapleorconfectcoarsewaterymaple?
Ten failed consecutive attempts to log in are definitely a red flag. If the legitimate user is so pressed to log in, they will resort to resetting their password as soon as possible.
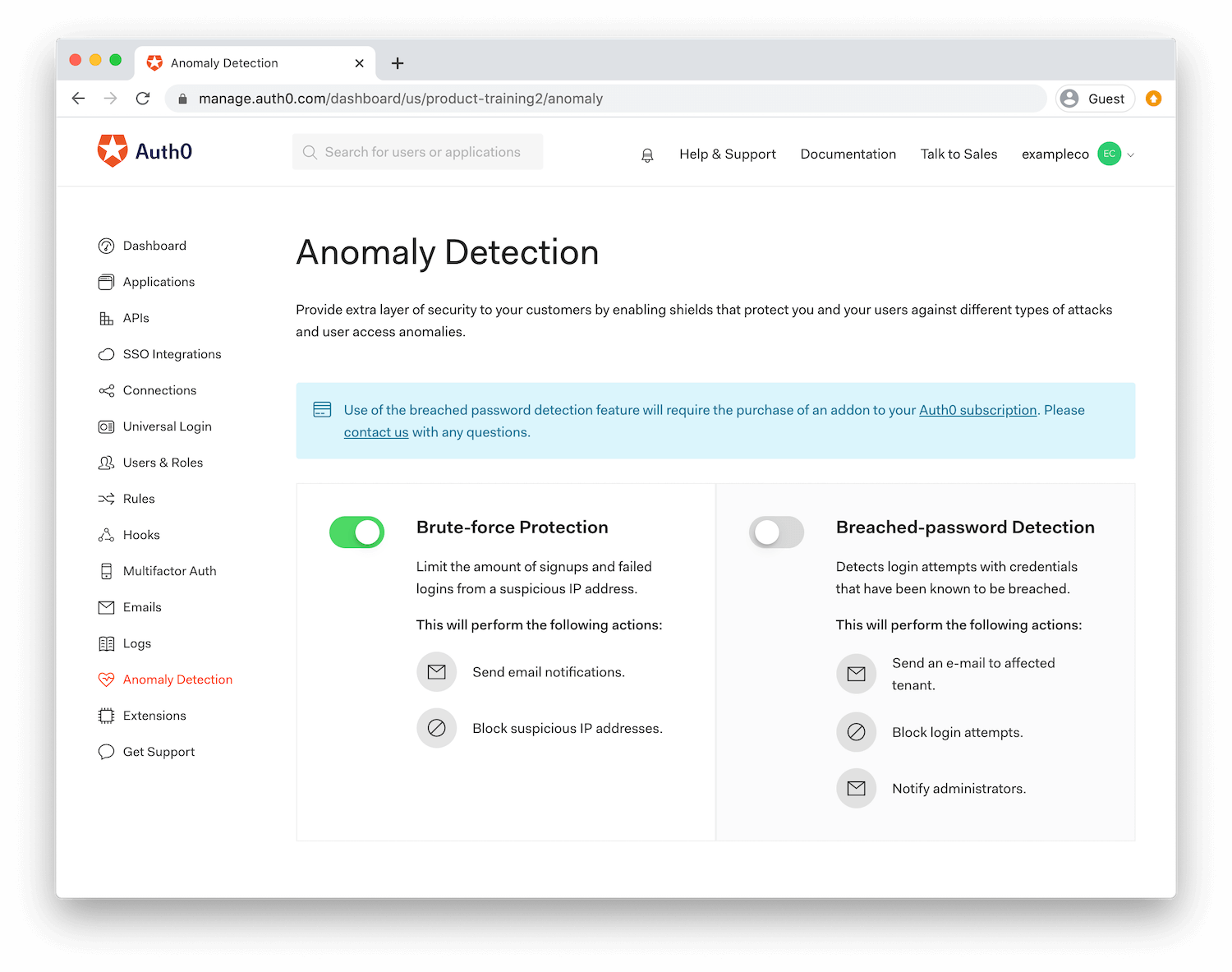
With Auth0, you can detect anomalies and stop malicious attempts to access your application. Auth0 offers two types of shields:
- Brute-force protection
- Breached password detection
A shield specifies the action you wish to take given a specific trigger. A trigger is a suspicious event that is detected when someone is trying to log in to your system, or they are using a breached password that has been reported by another third-party service.
Brute-force protection is enabled by default for all connections. There are two different triggers for the brute-force protection shield, for two slightly different attack scenarios:
- 10 consecutive failed login attempts for the same user and from the same IP address
- 100 failed login attempts from the same IP address in 24 hours or 50 sign up attempts per minute from the same IP address
Auth0 tracks large security breaches that are happening on major third-party sites to help keep your users and systems secure. By enabling breached password detection, when a trigger occurs, your users can be notified and/or blocked from logging in if we suspect their credentials were part of a published security breach. Auth0 never blocks the user itself, just the attempts from the suspicious origin.
Is love knocking at your door or is it a brute force attack? Integrate Auth0's anomaly detection in your application today to mitigate bad actors from forcing themselves into the heart of your data.
Happy Valentine's Day
Let Auth0 be the final piece that helps you build a secure and seamless user authentication experience that your customers will love to use. Get started with SSO, MFA, Universal Login, Anomaly Detection, and Rules for free today!
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.