Cross-industry fraud is on the rise. According to the fourth annual LexisNexis Fraud Mitigation Study, an increasing number of organizations are encountering fraud that has moved beyond its initial source and is causing damage in multiple arenas.
In 2018 89% of fraud professionals reported cases of cross-industry fraud — a five-point jump over the 84% who reported the same in 2017.
Hackers target particular industries — including insurance, financial services, health care, and even travel — that deal with a high volume of sensitive customer information. In many cases, companies in these spaces don't yet have adequate security protocols in place. As one example, less than half of insurance CEOs_ believe their teams are fully prepared for a cybersecurity event.
Once hackers obtain information from these targets, they’re able to use it to gain access to other higher-value accounts or platforms and conduct malicious activity across organizations.
This piece highlights the many, complex risks of cross-industry fraud — and offers solutions to help business leaders secure their organizations and end users.
"In 2018 89% of fraud professionals reported cases of cross-industry fraud — a five-point jump over the 84% who reported the same in 2017."
Tweet This
Cross-industry fraud can have extraordinary effects on end users
The uptick in cross-industry fraud presents a cascade of problems for company management. It's not always something they can isolate and solve for independently.
To start, these types of breaches often have extraordinary, negative effects on end users — relationships business leaders are trying hard to nurture. The ripple effect that occurs when identifying information stolen and used in cross-industry fraud makes it very difficult to detect where the breach originated and where it could move next.
This situation is further complicated by the fact that 83% of people use the same password for multiple sites. In many cases, hackers who obtain a username and password are able to move quickly by recycling them.
Credential stuffing and credit card skimming and shimming are two primary means by which hackers take sensitive data from its initial source and use it across numerous platforms.
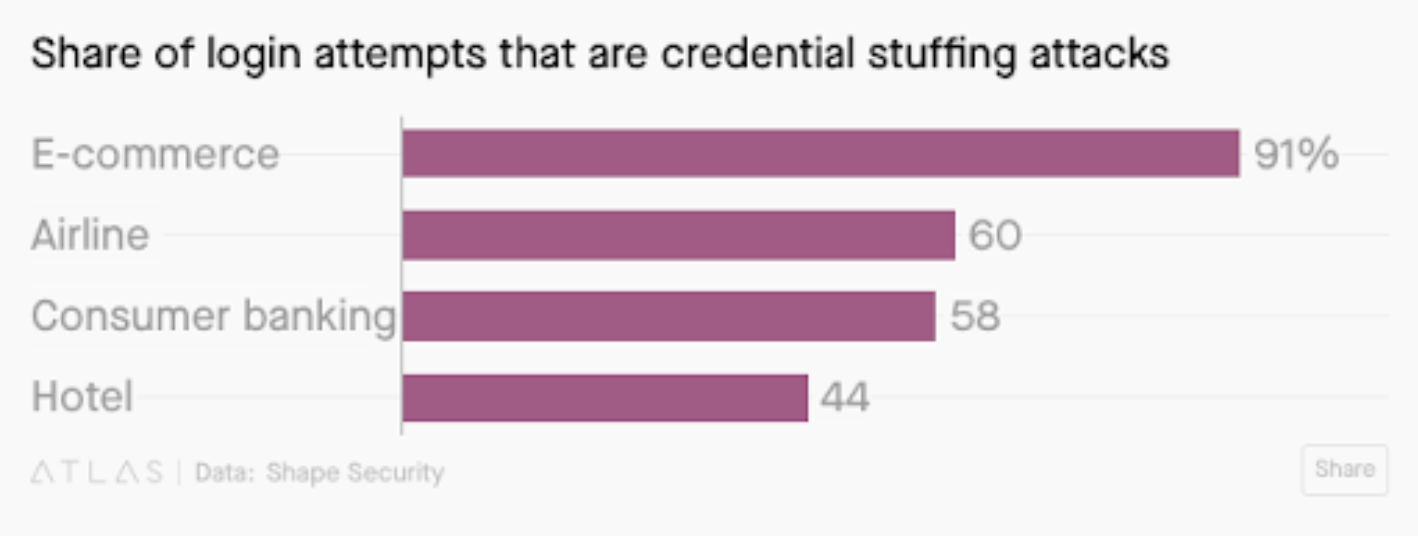
In our prior post, we described how cyber thieves use credential stuffing for a mass of login attempts at once. While these attacks are only successful about 3% of the time, they quickly add up. According to Quartz, 91% of login attempts on e-commerce sites are credential-stuffing attacks, followed by 60% on airline sites.
->
Credit card skimming and shimming (a newer technique designed to lift information from chip cards) is another method. When consumers make a purchase or visit an ATM, hackers are able to obtain credit card information and then sell that information on the dark web or make fraudulent purchases in numerous other industries.
In all sectors, cross-industry fraud brings with it a hefty price tag. In the same LexisNexis study, 80% of organizations reported that cross-industry fraud cases took a moderate to high financial toll on their businesses; more than half said they experienced extreme or high financial impact.
In turn, these unexpected costs can translate into an increase in the price of services for customers — a vicious cycle that punishes them rather than the hackers who are causing the problems in the first place. When you're trying to build trust, fraud in any form — even if it originated elsewhere — can do you harm.
Improving identity management to reduce cross-industry fraud
As cross-industry fraud continues to increase, it’s up to organizations to put security measures in place to protect their data and their consumers from these sorts of attacks.
1. CLOSELY MONITOR ALL USERS WITHIN YOUR SYSTEMS
A recent survey unveiled that 62% of employees recognize that they have access to company data they believe they shouldn’t see.
One of the best ways to protect business-critical information from unwanted eyes begins with implementing better user management. Cutting-edge user management tools and processes will help you exercise greater control over who’s able to access business-critical information.
->
A solution like Auth0, for example, allows your admins to closely track all of the users working with the company's systems and flag erratic behaviors, such as multiple failed login attempts. These admins can also grant permissions for specific users to access more sensitive data — while restricting the permissions of others.
2. INVEST IN ANOMALY DETECTION TO IDENTIFY SYSTEM-WIDE THREATS
It can take a long time to detect security breaches or threats. According to the Ponemon Institute, discovery takes an average of 197 days, which exposes your organization and your users to many vulnerabilities.
Having a solution like anomaly detection in place can alert you to unusual activity immediately.
->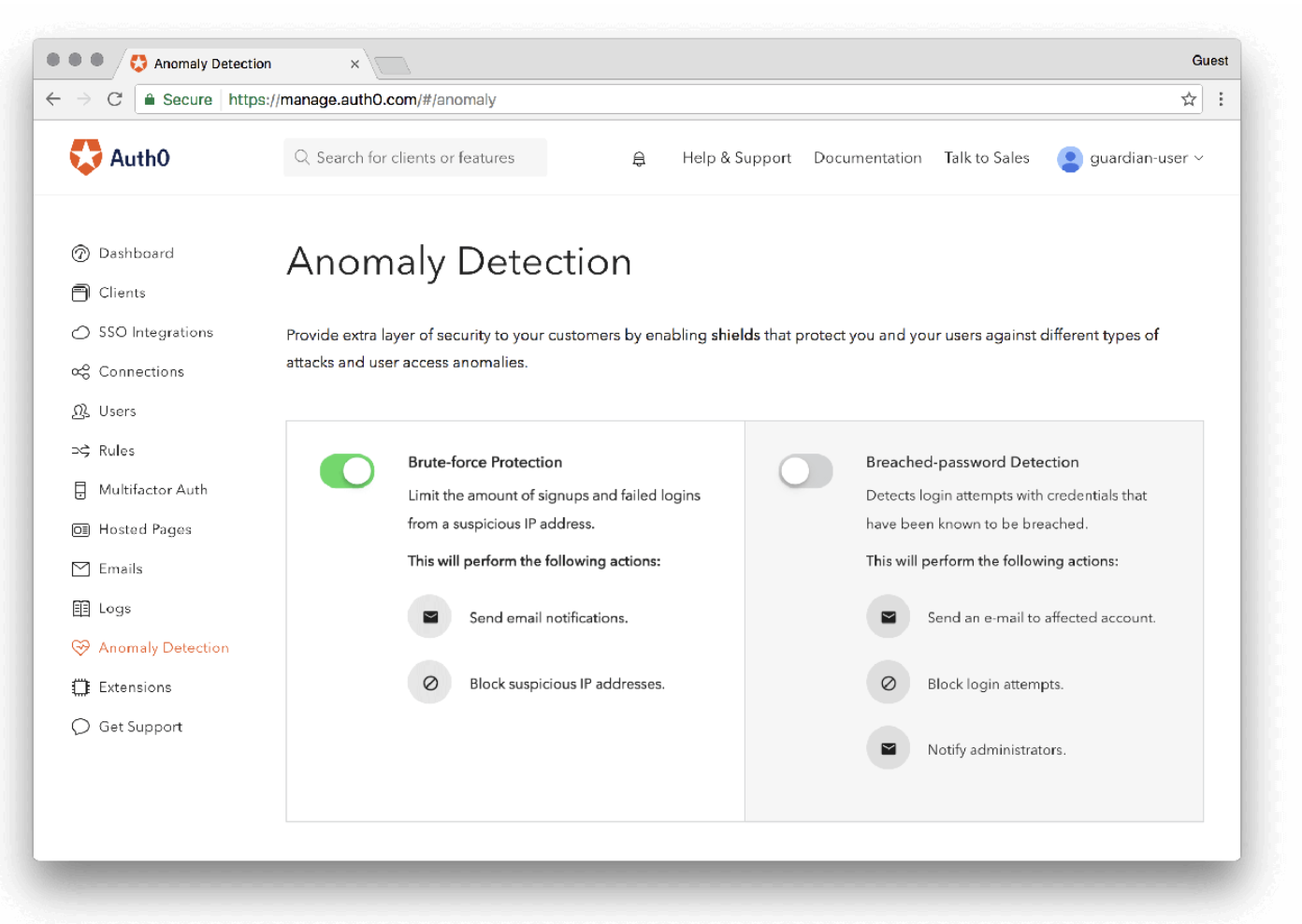
Auth0’s anomaly detection feature allows for brute-force protection and breached password detection, both of which you can easily turn on and customize from the main Dashboard view.
Brute force protection mitigates the risk that a hacker will push their way into your system by repeatedly iterating on a password until s/he finds the correct match, and breached password detection notifies your users when their credentials have been leaked by a third party data breach. In both scenarios, admins can block access and investigate the situation further.
"Auth0’s anomaly detection feature allows for brute-force protection and breached password detection."
Tweet This
3. DO AWAY WITH PASSWORDS
While the burden of identity protection falls largely on a company’s IT team, some of the effort rests with your users and customers. In an ideal world, they’d update their passwords when prompted (according to a new study by The National Institute of Standards and Technology) to ones that are longer and harder-to-guess.
Yet when users do make password changes, they’re often just slightly altered versions of their previous passwords (think something like “Password1” instead of just “Password”) — which leaves them just as vulnerable to attacks. A new report from SplashData shows that the two most popular passwords in 2018 were simply “123456” and “password” — essentially an open door for cyber theft.
Rather than counting on your users to keep themselves secure, institute streamlined login processes that also offer added security.
Auth0’s Passwordless allows users to log in using codes that are sent to their mobile phones — meaning they don’t need to remember or frequently update a password. What if people still insist on passwords? Auth0’s Breached Password Detection will alert you and your users immediately if their credentials are leaked.
Update your legacy systems to mitigate the risk of cross-industry fraud.
Fraud isn’t going anywhere. Even as security measures improve and technology advances, hackers will be motivated to rise to the challenge of stealing information and conducting malicious activity.
It’s up to you to make it as tough as possible for them to do so and protect your organization, your users, and your peers across industries who could be impacted by a breach.
Implementing a solution like Auth0 (https://auth0.com/) bolsters your security while it frees up your company’s time and resources so that you can focus on the tasks and projects that directly contribute to your revenue growth.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.






