The Capitol riot on January 6 was a dangerous moment on multiple levels, not least of which were the cybersecurity ramifications. The Capitol’s information infrastructure — laptops, documents, phones — were all in the hands of rioters for several hours. In one case, a woman allegedly stole a laptop or hard drive from Speaker of the House Nancy Pelosi’s office, though the woman eventually turned herself in to law enforcement.
The potential exposure of sensitive government information — especially coming on the heels of the devastating SolarWinds hack — is inspiring business leaders to examine their own cybersecurity vulnerabilities.
Many are asking: What would I do if my company’s tech was lost, stolen, or tampered with? How would we mitigate the damage from compromised hardware?
To start addressing those questions, it’s important to understand how a physical breach (of your offices or of your hardware) can have digital implications. Here are some of the cybersecurity lessons from the Capitol riot and how to protect your company in such an event.
All Physical Access Is Risky
There’s a famous cybersecurity truism that states, “If a bad actor has physical access to your computer, it’s not your computer anymore.” In other words, just because a mugger hasn’t run off with your laptop, that doesn’t mean it hasn’t been compromised. In the high-stakes world of corporate espionage (not to mention traditional espionage), all an attacker needs is a thumb drive and a moment alone with your device to steal information or introduce malware.
What’s more, in today’s hyperconnected world, computers aren’t the only risk vector since every network-connected device can present an entryway for attackers. The proliferation of devices on which we work has made it much more difficult to assess the damage after a potential security incident. Case in point: In the confusion of the Capitol riot, it was initially unclear how much hardware had been stolen or otherwise compromised. As Wired reported, “Rioters could have bugged congressional offices, exfiltrated data from unlocked computers, or installed malware on exposed devices.”
What to do if your hardware may have been breached
Let’s imagine a scenario in which there’s been a break-in at your office. There’s paper scattered everywhere, you’re not sure what devices are missing, and you’re not sure if the remaining tech is compromised. Where do you start damage control?
Don’t overreact
Don’t try to physically destroy every piece of hardware that could potentially be infected. That’s like ripping up all your floorboards to locate a single mouse.
Focus on securing user identity
The single greatest security threat of 2021 and beyond is a bad actor with stolen credentials. So make sure you’ve implemented multi-factor authentication (MFA), preferably using a strong method like biometric authentication or a hardware token.
In the wake of a breach, you should also change all your passwords. MFA will protect you from a password-based attack, but it isn’t foolproof, especially if an attacker has physical access to session cookies to perform session hijacking. But combining strong MFA, password rotation, and limited session lengths will help purge any bad actors from your system.
In all likelihood, your business will never face a physical breach like the capitol riot. But in the age of remote work, your organization’s physical assets are constantly in motion and exposed to risk. Given that fact, your network’s true perimeter is built into your networks: user identity.
Conduct an asset inventory
Maintain an asset inventory of all work-connected devices, and their vulnerability level is breached. Ideally, this is something you will have done prior to a security event, but if not, it should still be a priority. Establishing ownership of each device is a crucial part of asset inventory because without it, tracking down devices is much harder. Have every member of your staff report on the status of their own devices and whether or not they followed security protocols on those devices.
This will let you quickly determine if something is missing and help you figure out where to start looking for intrusions. For example, if Debra from accounting’s laptop is missing, and she had the password taped to it with a sticky note, that’s the first hole you’ll want to patch up.
My heart goes out to the unsung IT heroes at the Capitol tonight. My guess is they've never had to run asset inventory IR before - a daunting, stressful task in a tabletop exercise - and they're running one (prob w/o a playbook) following a full on assault of the Capitol.
— socially distant, mask wearing bat (@mzbat) January 7, 2021
Enterprises Need Standardized Data Security Policies
Within large organizations, data handling policies can vary from department to department and even from team to team. Some variation is inevitable since people use different devices and different applications and have different data sharing needs. But if your company doesn’t have some shared fundamentals of data security, fixing a breach becomes a daunting task. Large organizations need to establish a shared definition of what sensitive data means to them and what their legal obligations are under data privacy laws.
One of the biggest challenges in assessing the cybersecurity damage of the Capitol riot is that Congress has no standardized cybersecurity policies. Instead, Senate staffers told CNN that “while some IT protections exist across the organization, many decisions about information security practices are left up to individual lawmakers’ offices.” They report that some staffers do not use VPNs across all their devices, and some stored data locally on their desktops.
Capitol staffers also don’t seem to have had a shared definition of “sensitive data.” While elected officials are prohibited from sharing classified information outside of specific networks, it sometimes gets out anyway. Wired reports that “congressional staffers are not subject to Freedom of Information Act obligations and are often much more candid in their communications than other government officials.”
Even seemingly innocuous data can be dangerous in the hands of attackers, who can weaponize a high-ranking official’s (or executive’s) travel schedule. Bad actors can use personal information in spear-phishing attacks. Even device metadata can be extremely revealing if it shows who leaders are communicating with and when.
Protecting yourself and your company requires developing both technological safeguards and a shared culture of security.
How to implement tougher data security policies
Improving your organization’s cybersecurity requires C-suite supervision and buy-in at every level. Automate security whenever possible, instead of expecting your workforce to manage it during an emergency when they have other concerns. But while technical protections are crucial, don’t ignore the human element. Strong cybersecurity requires the active participation of an entire workforce and a shared awareness of potential risks.
Empower your CISO
Your head of security needs the support and resources necessary to implement top-down guidelines for the whole organization. This should take place in a larger context of the CISO’s evolving role and increasing responsibilities. To quote Andreessen Horowitz: “From its initial focus on securing on-premise servers, the Chief Security Officer (CSO/CISO) role has sprawled to include not just the cloud, but the physical workplace, individual laptops and phones, and data privacy and compliance.”
Part of the CISO’s role is to put security protocols in place so people can focus on their work. The CISO is also responsible for building an internal security culture that makes it easier for humans to choose security best practices whenever possible. Ideally, the rest of the C-Suite strongly supports them in all these efforts and models a commitment to security for the rest of the organization.
Have separate devices for work and personal use
This is a real challenge at companies with remote workforces and bring-your-own-device (BYOD) policies, but it’s one of the most effective ways to minimize damage in an attack. To convince your workforce to be disciplined about their device usage, emphasize the privacy benefits to them.
Brandon Maxwell, a Detection and Response Manager at Auth0, says, “If your device gets compromised by malware, an incident response engineer is going to have to analyze your downloads, your internet history, all those kinds of things.” In the case of a physical breach, an investigator may inspect the device for company data to ensure it wasn’t modified or accessed. While personal data would not be in scope, the analyst would likely see filenames and other metadata that an end-user may not be comfortable sharing otherwise. Emphasizing both privacy and security helps motivate employees to keep their devices separate.
Automate device lockouts
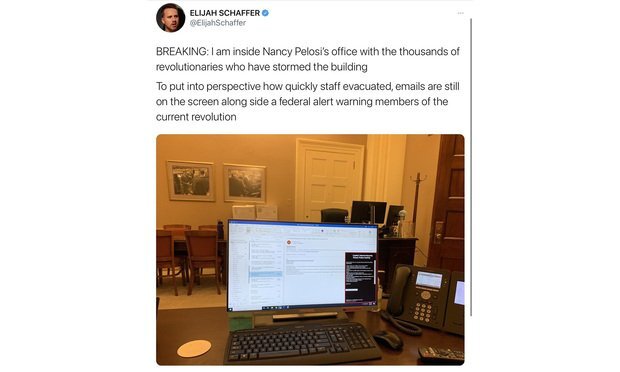
Institute centralized protocols to automatically lock devices after a short period of activity or if the hardware is missing. (Apple products include this capability as part of the “Find My” feature.) In an emergency, you can’t expect employees to lock their screens — it should happen automatically. Yet in the Capitol riots, numerous screens were left open, as you can see in this deleted tweet from one of the rioters.
Just as importantly, limit session length for employees. Just like your mobile banking app automatically logs you out after a brief period of inactivity, do the same with your sensitive data and applications. This can be useful even if you’re never the victim of an attack since locked devices also protect employees from their kids ordering $100 worth of apps while their back is turned.
You may also want to reconsider checking that “remember me for 30 days” box in your login screens since a bad actor who steals an unlocked or unencrypted device can then easily access that account.
Standardize physical, administrative, and technical controls across the organization
Practicing basic cybersecurity hygiene should be as deeply embedded in your company culture as your code of conduct. These expectations include things like requiring all remote workers to use full-tunnel VPNs on all devices. You should also implement strict password policies, guided by current NIST recommendations, and require all employees to use password managers to ensure strong and unique passwords.
Assume you’ve already been breached
Adopting this mentality will help you when going through monitoring logs for unauthorized access. Better yet, use an identity and access management (IAM) platform that adopts this mentality on your behalf and proactively demands MFA for users who exhibit suspicious behavior or for employees who use compromised credentials.
You Can Secure Your Data in a Chaotic World
The U.S. Capitol was put at risk not just by a failure of planning but a failure of imagination: the idea that “it can’t happen here.” Unfortunately, many organizations and businesses have the same attitude about their own cybersecurity, and it puts sensitive data at needless risk. By taking a sober look at the value of your own data and the threats to it, you can start building your defenses in case the unthinkable happens.
To learn more about how centralized identity and access management can be a part of your organization’s security posture, reach out to the team at Auth0.