If you work in cybersecurity or any computer-related field, sooner or later, you’ll have to explain public-key cryptography and digital signatures to non-technical people. With the recent rise of remote work and stories about system breaches, computer security has become a topic of discussion even among laypeople.
After trying to explain public-key cryptography and digital signatures to some clients with varying degrees of success, I wanted to develop an analogy that explained them and was easy to remember. I’ve found that even techies get confused by the formal definitions, and many non-technical explanations just seem unsatisfying.
That’s when I stumbled upon Panayotis Vryonis’ article, Public-key cryptography for non-geeks. It became my go-to analogy until my computer science professor, Dr. Robin Dawes pointed out a flaw. I refined it with his help, and a suggestion from Matthew Ernest, and the result is below. I hope you find it helpful when trying to explain these concepts to anyone!
The Box
Imagine a box with a special lock, as pictured below:

The lock has three positions:
- When the lock is at the “9:00” position, the box is locked, and its contents are inaccessible.
- When the lock is at the “12:00” position, the box is unlocked, which means you can open it and view its contents.
- When the lock is at the “3:00” position, the box is locked, and its contents are inaccessible.
In order to avoid wandering into endless “What if...?” tangents, assume that it’s prohibitively costly to pick the lock or break the box.
The Keys
There are two kinds of keys that work with the box’s lock.
The private key
The first kind of key belongs to you, and only you. You don’t share it with anyone else, which is why it’s called the private key. You might make a backup copy in case of emergencies, but you keep it in a safe place that only you know.

The private key fits the lock, but it has a particular limitation: it can only turn clockwise.

The public key
You treat the second kind of key very differently. Unlike the first key, you’ve made many, many copies of these keys. You’ve given them to everyone you know, and even people you don’t know. You’ve left them in as many public places as you could reach: restaurants, stores, busy streets, dark alleys, and any place you happened to pass through. You’ve even left them in other towns, and even other countries! Because of the way you treat this key, it’s called the public key.

Like the private key, public keys also fit the lock, and they also have a particular limitation — but in the opposite direction. They can only turn counterclockwise.

How They Work Together
The lock, private key, and public keys work together to produce these interesting outcomes:
- If the box is locked with a public key, only the private key can unlock it.
- If the box is locked with the private key, only a public key can unlock it.
The keys are designed so that you can’t use one key to figure out how to make the other key.
We can use the box and keys to create two useful kinds of secure communication:
- I can send you a secret message.
- You can send me a message with proof that you (and not some impostor) sent it and that it wasn’t altered en route.
Let’s take a closer look at each of these kinds of secure communication.
Sending Secret Messages
Suppose I wanted to send you a message that I wanted only you to read. We have enemies in common who’d love nothing more than to know what’s in the messages I send you.
We each have a cadre of minions to deliver our messages. We trust them... to a limited extent. It would be all too easy for our foes to intercept our messages through force or bribery.
There must be a way to send messages to you secretly, and that’s where the box comes in. I can use the box to send the message so that no one but you can read it.
You have the only private key. Everyone else has at least one of the public keys because you’ve been giving them away like candy.
I put my message in the open box. Since it’s open, it’s unlocked, which means the lock is at the “12:00” position.
I use one of the many copies of the public key that I own to lock it, turning it counterclockwise from the unlocked “12:00” position to the locked “9:00” position.

The message is now ready for a minion to deliver to you.
I’m not worried that my minion or anyone other than you will be able to read the message while it’s in transit. Even though anyone can easily find the public key, they can’t use it to unlock the box. Only the private key can unlock the box if it’s been locked with the public key.
When you receive the box, you use the private key to unlock it, turning the key clockwise from the “3:00” position to the “12:00” position.
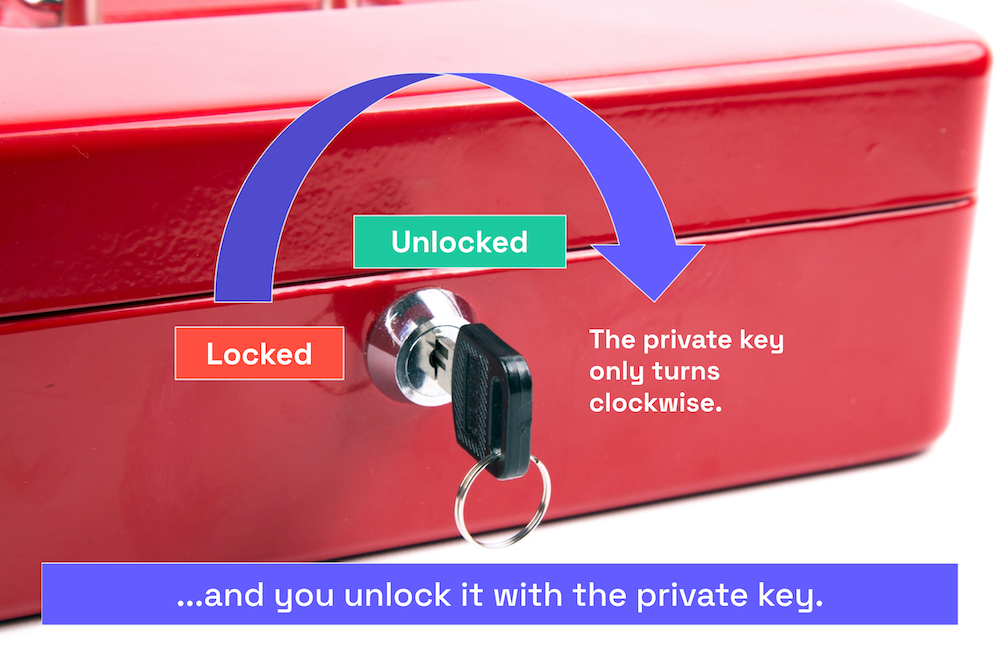
In summary: to send you a secret message, I use a public key to lock the message so nobody can read it, and you use a private key to unlock the message so that you can read it.
This is the general idea behind public-key encryption: encrypt with the public key, decrypt with the private key.
Signing Messages
The “secret messages” use case for the box and private and public keys is intuitive: anyone with a public key can lock a message, but only the holder of the private key can unlock it.
There’s another way to use the box and keys: you can lock a message with the private key, which anyone with the public key can unlock. What could a possible use case there be for a system where anyone can unlock the box?
Suppose one of our common enemies has been trying to break up our alliance and that I’ve been receiving very hurtful messages that appear to have come from you. (I’ll leave the content of those messages to your imagination.)
That enemy has either been sending fake messages or has been intercepting and altering your real ones. There has to be a way to package a message in order to prove that it’s actually from you!
There is a way: the box!
In this scenario, you put your message in the open box. Since it’s open, it’s unlocked, which means the lock is at the “12:00” position.
Using the private key, you “sign” the message by locking it, turning the key counterclockwise from the “12:00” position to the “9:00” position.
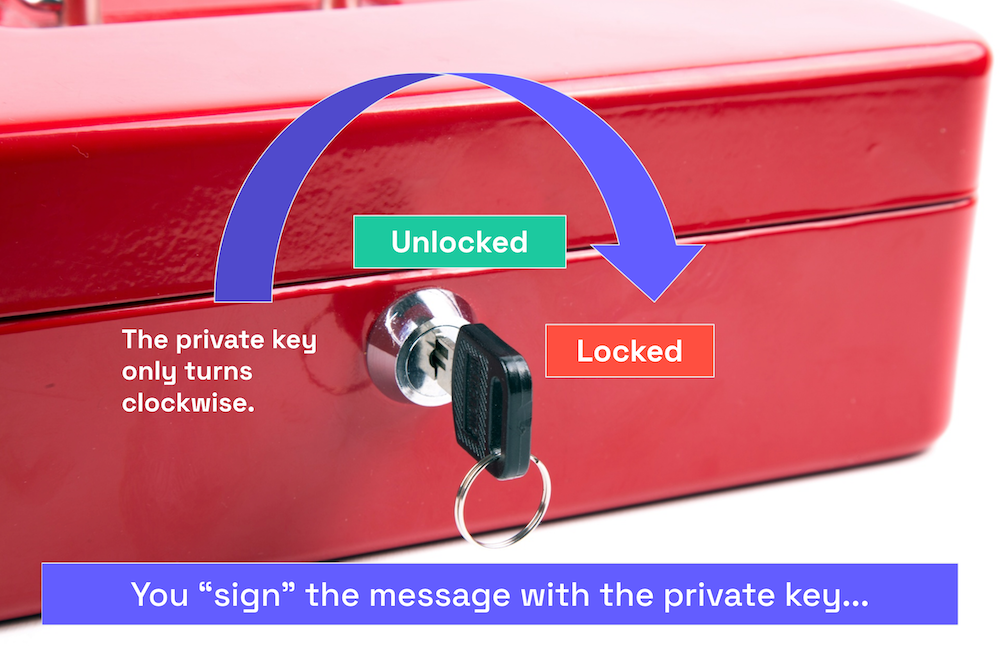
One of your minions delivers the box to me.
Since you locked the box with the private key, anyone can unlock it with any one of the many public keys you have distributed. Our common enemy, knowing that this message is in transit, could intercept it and replace your invitation to tea with a “top ten” list of very cutting insults that would surely dissolve our alliance.
The problem with the enemy’s plan is that it won’t work. Intercepting and altering the message means that they would have to do one of two things before forwarding the box to me.
- They could leave the box unlocked. Since the box is supposed to arrive locked, this is an obvious sign that the message may have been tampered with.
- They could lock the box. They would have to do it with a public key, which means that only the private key can unlock it. I wouldn’t be able to unlock the box with the only key I had — the public key — which would lead me to conclude that someone had unlocked the box before I did.
If the box arrives at my doorstep and...
- It’s locked
- I can unlock it with the public key
...then, I can be assured that the message came from you and wasn’t changed en route.

In summary: to send me a message with proof that you are the sender, you use the private key to lock the message. You’re the only person with the private key, and only a public key can unlock messages locked with the private key. If one of the public keys can unlock that message, I know that it came from you.
This is the general idea behind digital signatures: sign with the private key, verify with a public key.
How About Sending a Message That’s Both Secret and Signed?
You might think that sending a message that is both secret and signed is paranoid. I would answer by saying, “Paranoia is the mistaken impression that people are out to get you.”
Suppose I wanted to send you a secret signed message. I could do it with two boxes:
- A smaller box, which I own. It will prove that I sent the message. I have the private key for this box, and you have one of its public keys.
- A larger box, which you own. It will keep the message secret. You have the private key for this box, and I have one of its public keys.
I would lock the message in my smaller box using my private key and then lock it in your larger box using your public key.
When you receive the delivery, you will unlock your larger box first, using your private key. This would reveal my smaller box inside, which you would unlock with my public key.
It’s Not Keys and Boxes, but Numbers and Algorithms
Of course, we’re not really dealing with boxes, keys (at least the kind that goes into locks), or minions. Here’s a list of elements in these stories and their real-world equivalents:
- The message: Anything that you’d want to send that can you can view or edit with a computer. It could be text, one or more pictures, an audio or video recording, a database, or even an application. As far as the computer is concerned, messages are just a long series of numbers.
- The private and public keys: Very large numbers that are used in a lengthy math process to encrypt, decrypt, sign, and verify messages.
- The box: An algorithm that takes the message and keys and performs the math process to encrypt, decrypt, sign, and verify messages.
- Minions: The way in which the message is sent. This could be the internet but could just as easily be an actual minion, such as an unsuspecting summer intern with a USB key.
In the alternate universe where messages are sent with boxes and keys, everyone would have their own set of boxes with their own private keys, as well as copies of other people’s public keys. In the real world, we run applications that run public-key encryption and digital signature algorithms to secure our messages. We still use public and private keys in the real world; they’re just digital.





