Financial institutions are under intense scrutiny by regulators as well as customers to be sure that their user data is secure. Legal pressures are mounting, and customers are increasingly vocal and demanding that companies are more transparent and responsible with their information. Finance, over and above other industries, demands a higher level of protection. Behemoth institutions like J.P. Morgan and Equifax continue to be top targets for cybercriminals.
One concrete step that these institutions, along with smaller firms, can take is to secure their consumer apps. Traditionally, apps with authentication systems require users to provide a single identifier, such as an email address, username, or phone number, along with a correct password or pin to gain access; however, with financial apps, this isn't always enough.
Two-factor authentication or 2FA adds an additional step to the process. Like a double security door — if a thief unlocks the first one, he's blocked by another.
Breaking Down Common 2FA Approaches
In general, there are three factors in authentication:
- Something you know (such as a password you created)
- Something you have (such as a cell phone or other piece of hardware)
- Something you are (such as your fingerprint, gait, or facial features)
Two-factor authentication requires that you have two of these options. In addition to a password that you “know,” 2FA can request you “have” a cell phone or other device handy for a TOTP (a time-based one-time password algorithm) or that you present a biometric, such as a thumbprint.
Time-based one-time password algorithm (TOTP)
A time-based one-time password algorithm or TOTP generates one short-lived (~30 seconds or less) password from a secret key in combination with a current timestamp. A cryptographic hash function connects these two.
The Microsoft Authenticator is a common option that generates a TOTP:
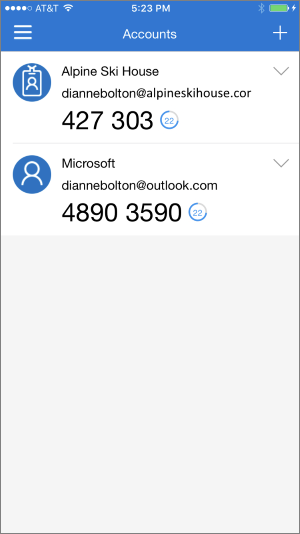
Prior to logging into an app, users will go to Microsoft Authenticator, generate their code, and, before it expires, use it to log into the app. Other leaders in the space include the Google Authenticator, along with smaller providers like Twilio, Authy, Duo Mobile, and the LastPass Authenticator. These providers offer 2FA solutions for both mobile and desktop platforms.
Biometrics
Biometrics have made big strides in recent years, including the launch of Apple’s iPhone X facial recognition feature. Widely used biometrics for identity verification include iris or retina recognition, facial, fingerprint, hand, and even DNA usage.
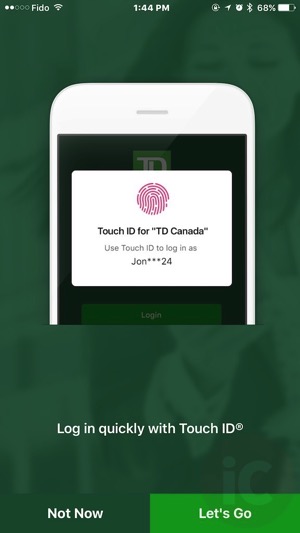
Many consumer financial apps, like TD Bank's app for basic checking, savings, and transfer options, employ the thumbprint as a second authenticator:
Users are prompted to place their thumb on the home button for identification prior to entering the app. Several established firms, including Vanguard and other asset managers, have incorporated Touch ID as well as voice verification for certain transactions.
"Despite the proven ability of 2FA to reduce the threat of a security breach, the trick is getting users to opt in."
Tweet This
The Challenge: Get Users to Opt In
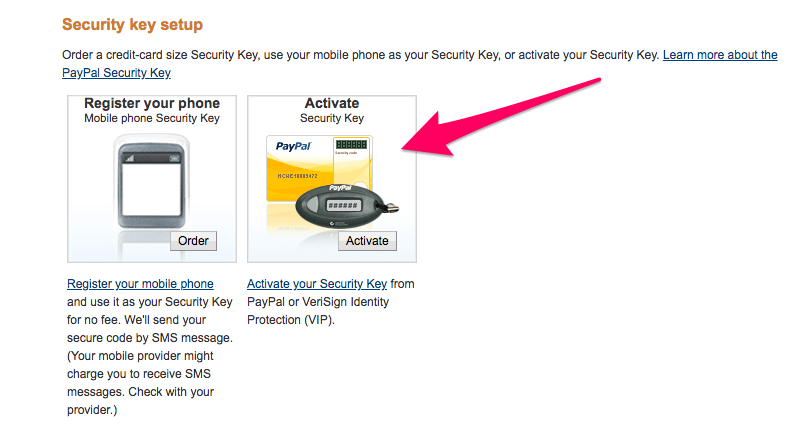
Despite the proven ability of 2FA to reduce the threat of a security breach along with the ease of setup (no advanced security or developer skills are required), 2FA has yet to become mainstream. It can be unclear for many users how to set up 2FA. For example, with services like PayPal-for-my-paypal-powered-by-braintree-user-faq3500), users have to log into their control panel, navigate to their account, and enable 2FA with a QR code or another supported app:
It can be difficult for a user without 2FA knowledge to know which option to choose — after already puzzling out how to get to this stage without clear directions in the first place. While some may opt for SMS (first option), the second option (TOTP) doesn't rely on incoming text messages and has proven to be more secure.
For financial firms looking to gain customer trust, making the 2FA setup simple (or figuring out a way to integrate it into their app's UX in a seamless way) will go a long way toward distinguishing themselves from the pack. Customers are particularly looking for a high level of security with their financial information. If you can clearly communicate your enhanced strategy, you will gain a competitive advantage.
"Customer happiness and high engagement are the biggest determinants of its success."
Tweet This
Discourage Password Use
One way to help users understand the importance of 2FA is to discourage the use of passwords alone. Passwords are historically vulnerable due to human error (we're often lazy about re-creating lengthy, secure, and unique passwords and instead recycle the same or iterations of the same password for the majority of accounts) and the ease with which hackers can access this first level of authentication. Explaining that breaches of personal information happen daily — due to phishing and additional criminal tactics that get the user to unknowingly reveal their password — can prompt your customers to consider an alternative. While a password manager is one option, 2FA brings another dimension to the security game altogether. If one or multiple passwords are compromised, a hacker still cannot access the account without acquiring the second factor.
Balance UX and Practicality
In many cases, customer happiness with a new feature and a high level of engagement with it are the most important determinants of its success. With cybersecurity features, however, where do you draw the line between ease and enjoyment of use and practicality? Should something so critical be fun? Do users want to see the same types of design for 2FA integrations that they see with, say, e-commerce apps? You don't necessarily have to sacrifice a pleasant user experience due to the serious nature of a 2FA feature; at the same time, you should be conscious that 2FA is distinct in its functionality. Consider a design that is utilitarian, clear, and makes the user understand the power behind the tool.
The Google Authenticator, for example, balances clarity, capability, and a splash of color:
Whichever authenticator tool you offer your users it should reflect your brand and focus. Further reading on the topic that we've found helpful includes:
- UX vs. Cybersecurity
- Cyber Security Requires an Important Ingredient: Strong UX
- What is two-factor authentication, and which 2FA apps are best?
Conclusion: Be There for Your Customers
Figuring out how to integrate 2FA into your consumer financial apps in ways that will make your customers opt-in and enjoy the process will give them peace of mind, help ensure your firm is compliant, and even allow you a competitive advantage in the race to gain user support and trust.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.