TL:DR: Digital identities have emerged as a crucial aspect of an online existence. From buying a product online, logging into a streaming service, or communicating with friends via social media, digital identity is a fundamental component in each of these activities. At the same time, companies must ensure digital identities are safe from malicious actors without adding friction for trusted users. This blog outlines how device intelligence can play a crucial role in protecting digital identities from fraud and optimizing the user experience.
The Role of Digital Identity
A digital identity encompasses the data and information that represents an individual, organization, or device online. It plays a pivotal role in how a person interacts, transacts, and takes advantage of the digital world.
Successful validation of a digital identity enables one to perform associated actions and transactions for the service being used, such as updating account information or authorizing a banking transaction. However, malicious actors target these digital identities to commit fraudulent transactions or steal valuable data, which has left many users lacking trust and confidence in the security of their online accounts.
Types of Digital Identity Fraud
- New Account Fraud
New account fraud (or fake accounts) occurs when users sign-up more than once to receive one-time bonuses or promotional offers as a reward for becoming an account holder but with an ulterior motive. - Account Takeover (ATO)
Account takeover occurs when malicious actors steal login credentials to access someone else's account. Once fraudsters have access, these accounts can be used to conduct various activities, such as transferring funds or accessing personal data. - Social Engineering
Social engineering is a deceptive and manipulative technique used by cybercriminals to gain unauthorized access to sensitive information; instead of relying on technical vulnerabilities, social engineering preys on people's trust, curiosity, and willingness to help. It often takes the form of phishing emails, pretexting phone calls, or impersonation tactics, tricking individuals into divulging confidential data or performing actions that compromise security. In September 2022, Uber's private network was breached by a teenage hacker who used social engineering methods to gain secure information from an engineer.
What about Multi-Factor Authentication (MFA)?
Product teams are conscientious about adding additional layers of friction to secure user accounts, fearful that they will abandon the transaction or sign-up process, resulting in a loss of revenue. This typically means that MFA is not mandated and is optional for the user. Even when users opt-in or MFA is enforced, companies are still relying on weak or outdated MFA methods, such as SMS/email one-time password (OTP) or cookie-based MFA, which can easily be phished or spoofed.
Strong MFA is an effective defense layer to help secure user accounts, given how easy it is to steal a user's password. However, many companies are challenged with how to make accurate and context-based MFA decisions that reduce friction for genuine users. Most forms of context-based authentication rely on IP addresses or cookies, which on their own are not stable or reliable enough to ensure the trust required to skip the MFA stage.
As a result of the above challenges, most companies fall back to challenging all authentication transactions with MFA, resulting in unnecessary user friction and rising SMS OTP costs.
How Device Intelligence Protects Accounts
Accurate device intelligence recognizes trusted users from bad actors. Generating an accurate and stable device identifier during account creation or the next trusted login results in the user having a list of “trusted devices”. If an authentication attempt is initiated from a “new” device not within that list, the attempt can be blocked or challenged with a strong MFA factor. When the actual user returns and authenticates from a “trusted device,” you have a high degree of confidence it is actually the owner of the account and can, therefore, skip any additional friction, which leads to an enhanced, seamless user experience.
Capturing device intelligence data for each account creation request allows you to make smart decisions on whether or not to allow account creation. During the creation process, if the device identifier captured already exists for a registered user, depending on your allowed account-to-device ratio, you can block or allow the sign-up request.
Companies who are using device intelligence are able to block malicious actors from using their services by adding them to a block list, as they can easily identify when they have attempted to create multiple fake accounts (for the purpose of promo abuse or SMS pumping) or attempted account takeover attacks using their device/browser or browser automation tools (bots).
Why Fingerprint with Auth0
Fingerprint was built to help companies solve complex identity & fraud-based challenges. Fingerprint is an API-based solution, which makes it very easy to plug into Auth0’s well-known Extensibility.
Using Fingerprint in addition to Auth0 Security modules layers in an extra level of defense to help keep your Auth0 tenant safe from synthetic account creation and account takeovers. This is achieved by adding Fingerprint’s unique device fingerprint to the Auth0 user profile for each user at signup or a trusted login. Fingerprint’s visitor identifier is 99.5% accurate at identifying returning visitors; it can then be used to evaluate the identity of the device that is attempting to authenticate.
See the example flow below for preventing account takeovers:
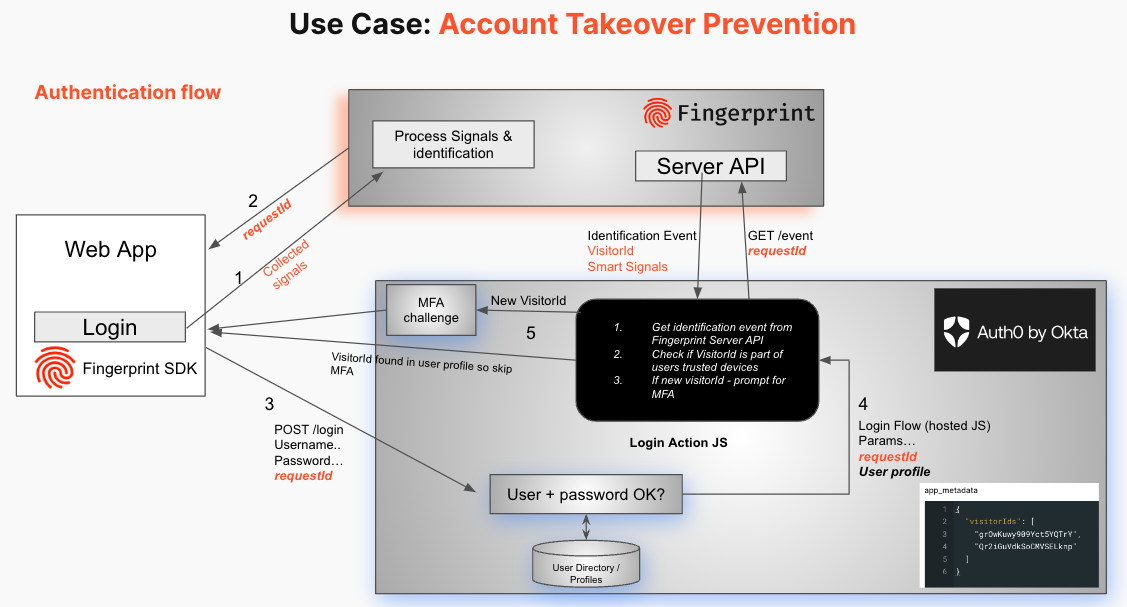
In addition to device identification, Fingerprint also provides Smart Signals, such as bot detection, VPN detection, and browser tampering detection, that pinpoint indicators of fraud from anonymous traffic. All of these Smart Signals can be evaluated in Auth0’s extensible Actions within the sign-up or login flows.
You can find additional details and technical integration documentation in the Auth0 Marketplace Fingerprint listing.
Conclusion
One of the key use cases for implementing a device intelligence platform is to prevent fraud, and as discussed above, digital identities are prime targets for types of fraud, such as signup abuse, account takeover, and social engineering.
Unique, stable, and accurate device identifiers from Fingerprint recognize good users from bad users and block the activity associated with bad actors as a result. Accurately identifying the devices of your good users and incorporating them with Auth0 Actions allows you to make smart decisions to keep accounts secure with no additional friction.
To get started, sign up for your free Fingerprint trial here and check out the Auth0 Marketplace Fingerprint listing for more details on how these solutions work together to help you stop fraud without friction.





