The ability to clearly observe, track, and log in as your authorized users allows for the swift implementation of updates and early alerts of any suspicious behavior.
Moving to a hybrid cloud model is the first step that many companies take when undergoing a digital transformation. Less expensive and resource-intense than a full private cloud option — yet still providing an extra measure of security, compared with the public cloud — hybrid deployment has become highly popular among tech professionals.
Yet once you migrate to a hybrid cloud model, it can become increasingly difficult to keep track of your users. Previously, your team likely conducted critical tasks on-premises. Now, with the opportunity for multiple users to log in and work with sensitive data from a range of locations and devices, keeping tabs on authentications (who has signed in) and authorizations (who has permission to use private resources) becomes essential.
A clear identity management system can help your team organize user information in a way that makes it easy for administrators to have a birds-eye view of actions taking place and make quick changes if need be. You can build this yourself or outsource your identity and access management (IAM) needs to ensure they are professional, up-to-date, and don't cause additional security concerns.
Track Your Users in the Hybrid Cloud
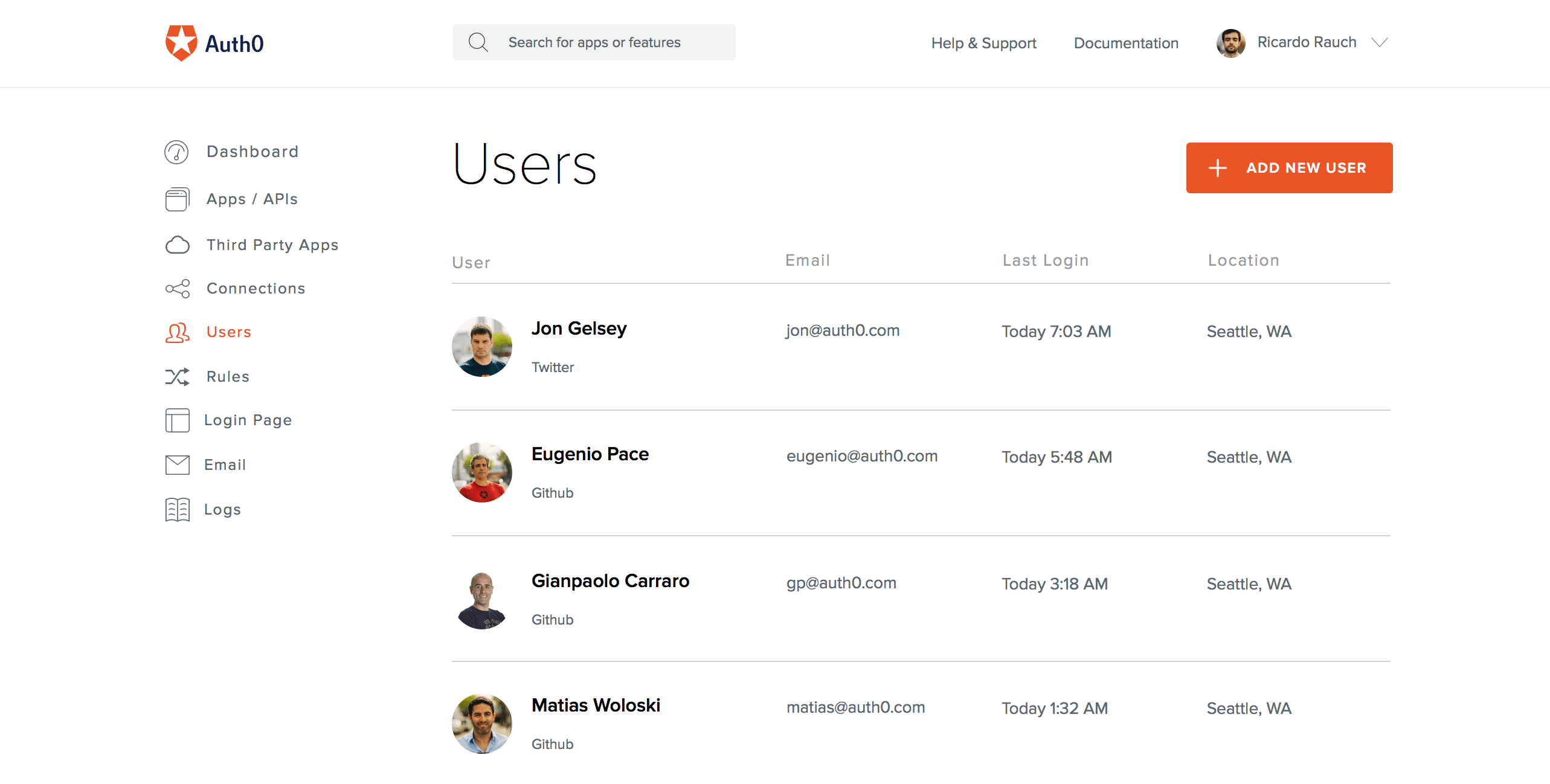
A robust IAM strategy can show you who is currently logged into your network. Having the full picture is essential to staying organized and rooting out any suspicious activity. For example, Auth0 provides a simple, efficient dashboard to centralize a range of user interface tools.
With this, an administrator is able to view all current users, their locations, login history, and additional personal information. From here administrators are able to supervise password resets, block and delete users, and perform a range of other tasks.
After granting a new member access, the administrator can simply add a user and create his or her profile, populating it with further details:
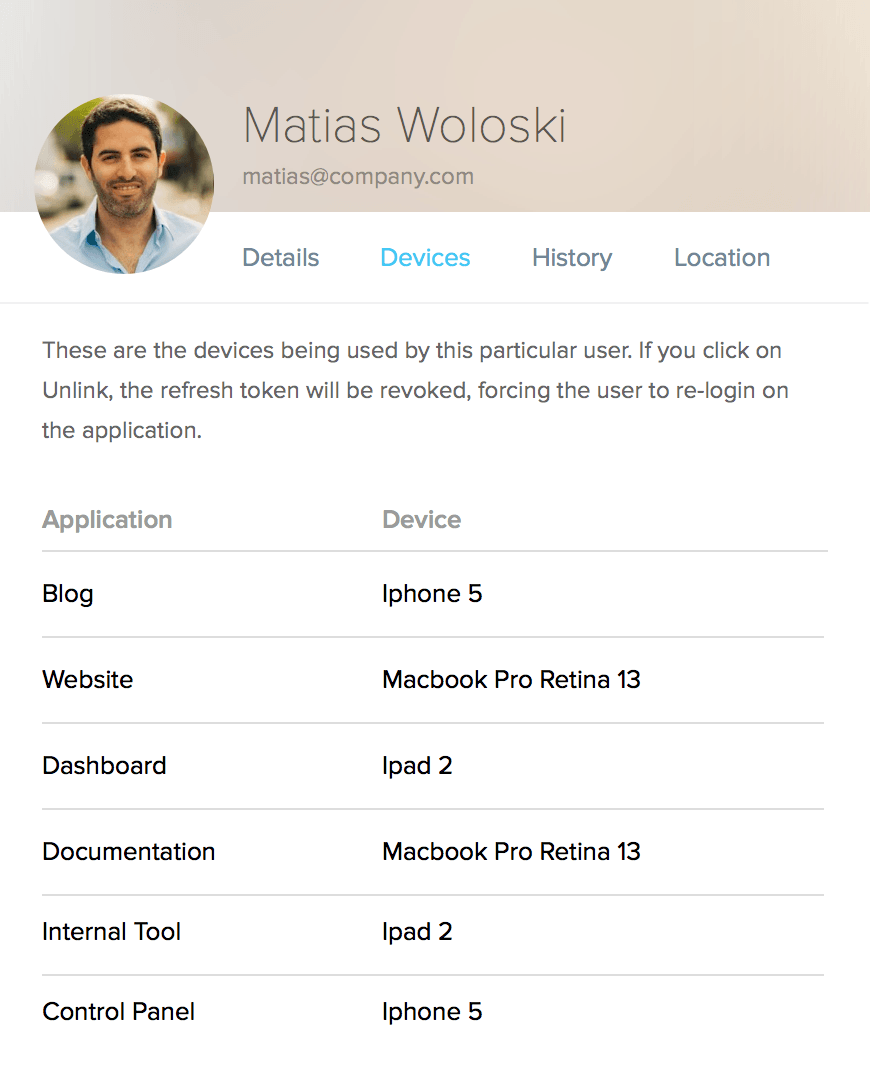
The above profile breaks down all devices the administrator has authorized for this particular user. This allows the administrator to confirm that the user is accessing any private data from an approved source. If the administrator has any questions about a user's behavior, he or she may unlink a particular device at any time.
"A robust IAM strategy can show you who is currently logged into your network. Having the full picture is essential to staying organized and rooting out any suspicious activity."
Tweet This
Restrict Access to Sensitive Documents
In the hybrid cloud, your workflow is split between confidential tasks in the private cloud and less sensitive ones in the public cloud. With a strong IAM system, you can allow access to private documents based on a user's ID. This can limit the amount of damage that can occur if someone's username or login details are stolen. IAM companies like Auth0 facilitate different permissions based on the user.
To make the task more efficient, Auth0's authorization extension allows you to combine your users and give permission such as “approve:reports” to an entire group. As you can see above, several permissions can be created within each application, allowing administrators to assert control over nearly all actions taking place on their network.
Only a highly detailed identity management system will truly help you unlock the potential of the private portion of your hybrid cloud system.
Conclusion: When to Shift to the Hybrid Cloud
While the hybrid cloud has enormous advantages, such as the ability to quickly scale alongside your growing company, it isn't appropriate for all organizations. Setting up your own servers on the private end of the hybrid cloud can be costly, hindering teams with small computing budgets. Major cloud service providers like Amazon Web Services, Google Cloud, and Microsoft Azure can offer a certain level of intrusion monitoring in a basic public cloud option, which can often provide enough security for smaller teams.
However, if your company has the funds, moving to the hybrid cloud can allow your most business-critical applications to remain behind an additional firewall. Creating or outsourcing a strong identity management system to better monitor and control your users in the hybrid cloud will open even further opportunities to fix bugs and root out unusual log-ins as your company continues to grow.