Every organization that uses a login box must have some form of identity and access management (IAM) system to keep track of users and control access to data and services. But in recent years, managing identity has become more complex. Today, identity management is inextricably bound to issues of security, user experience (UX), and scalability.
To cope with the challenge of maintaining IAM systems, more and more organizations are turning to Identity-as-a-Service (IDaaS) providers.
But what exactly is Identity-as-a-Service? What do these providers offer that can help businesses navigate such a challenging environment?
In this piece, we’ll define identity as a service — its core components and the reasons why it’s a rapidly growing segment of Software-as-a-Service (SaaS).
IDaaS Defined
When an organization creates or updates an application, they have to choose which functionalities to write themselves and which to entrust to a third party. For instance, if you’re writing an application that takes payments, it’s often more time- and cost-effective to use a platform like Square rather than making your own payment system from scratch.
The same holds true if your application requires users to log in. Given the complexities of logins and the many ways that identity management touches on analytics and security, it’s often simplest to purchase an IDaaS solution that integrates into your software and handles these issues for you.
IDaaS providers offer cloud-based solutions for IAM functions.
When you purchase an IDaaS service, you’re essentially purchasing an API (Application Programming Interface). In the simplest terms, an API is a set of programmed rules for how software components or applications interact, like a translator or mediator.
In the case of IDaaS, the API mediates the authentication flow between the end-user and the customer’s application(s). IDaaS may also be used to mediate Authorization to certain areas of the application or to access certain data within the application(s) your company is building.
When we talk about managing identity, we’re referring to the identities of three basic classes of users:
- Customer identity and access management (CIAM), which applies to end-users.
- Workforce IAM, which manages your staff and their access to internal applications.
- B2B IAM, which lets businesses integrate identity with their business partners and enterprise customers.
Each of these classes requires a different approach, and an organization may subscribe to an IDaaS provider for all of them or just one.
There are a few core features common to virtually all IDaaS providers. These include:
- Multi-factor authentication (MFA)
- Biometrics
- Single Sign-On (SSO)
- User management and access control
We’ll get deeper into all those terms below.
Multi-Factor Authentication (MFA)
MFA is an increasingly popular way of verifying a user’s identity. It’s more secure than the traditional username/password method of logging in since passwords are vulnerable to multiple types of attacks.
MFA requires users to log in with more than one piece of identifying information (i.e., a push notification in addition to a password).
Users must share some combination of the following credentials to log in:
- Knowledge: Something the user knows (such as a password)
- Possession: Something the user has (such as a cell phone)
- Inheritance: Something the user is (such as a fingerprint or retina scan)
The most common form of MFA is two-factor authentication (2FA), though you may customize an MFA solution to ask for more credentials depending on the security risk.
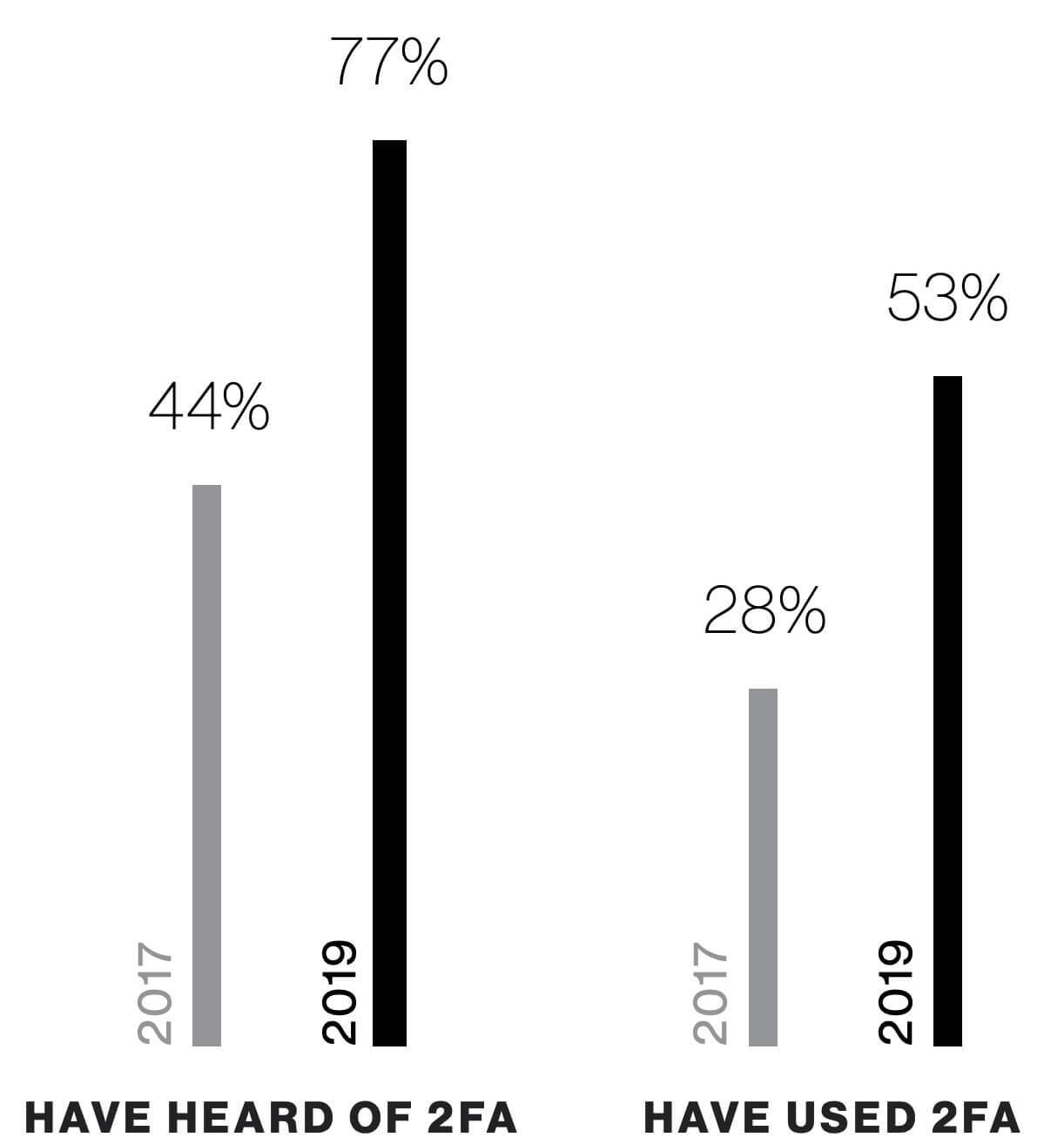
Despite numerous reports on the benefits of multi-factor authentication for stopping data breaches, widespread adoption is still surprisingly low — though it has increased significantly in recent years:
One of the reasons for the lagging adoption rate is that designers are wary of creating extra friction at login, especially for B2C authentication. But third-party IDaaS providers offer more customizable MFA options, like step-up or adaptive authentication. These approaches to MFA only ask for extra credentials if a user meets a certain risk profile; for instance, logging in from a new IP address or changing payment information.
Biometrics
Biometrics means the use of an “inheritance” criteria — something the user is as a means of verification. If you’ve ever unlocked your smartphone with your thumbprint, you’re familiar with biometrics.
In addition to thumbprints, other biometric authentication methods include iris or retina recognition, full facial recognition, fingerprint, hand, and DNA usage.
Many organizations are excited to use this technology and have turned to IDaaS providers to implement it rather than trying to train their in-house teams on this specialized branch of knowledge.
Single Sign-On (SSO)
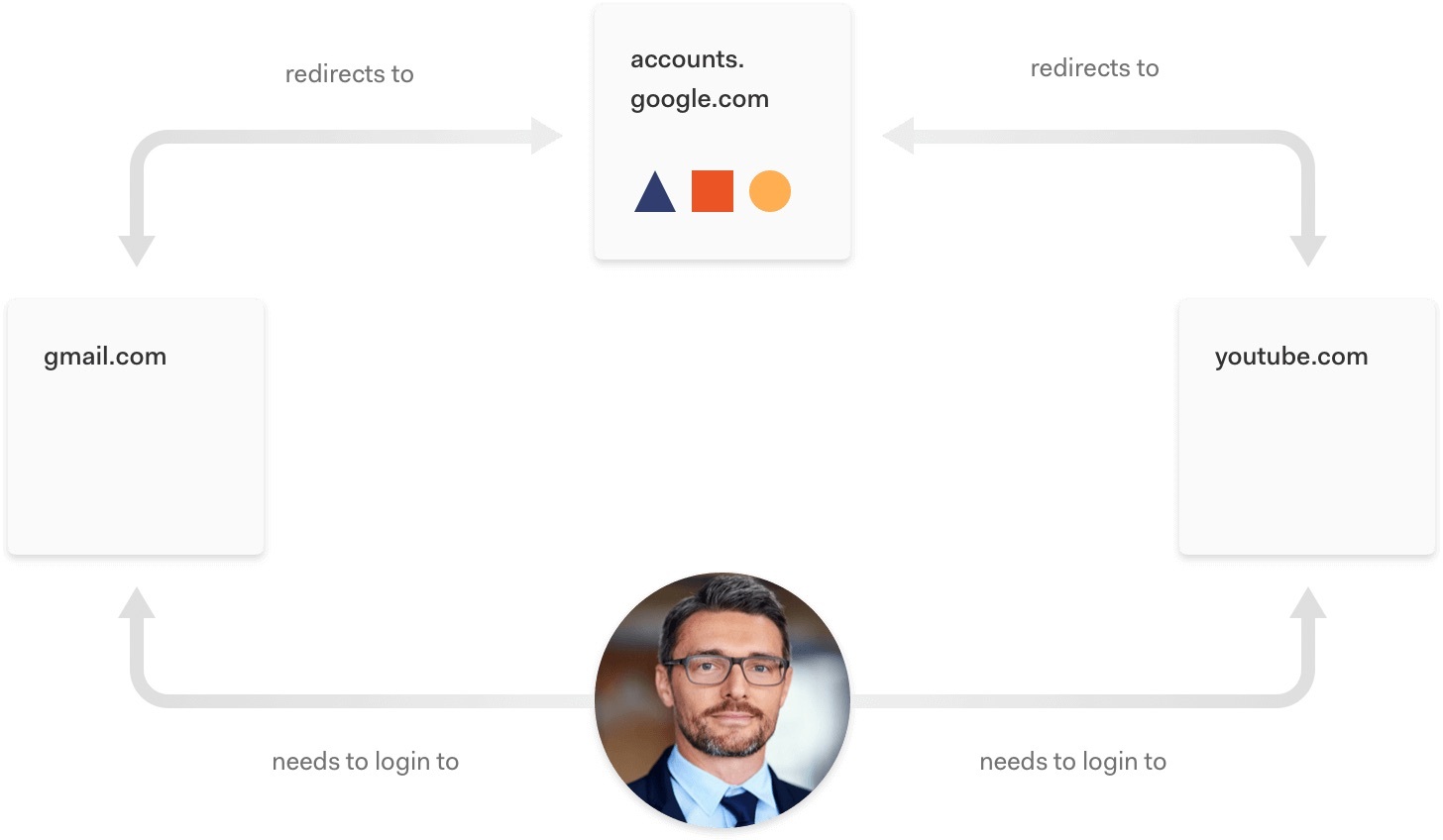
Single Sign-On (SSO) allows users to log in to one application and then automatically be logged in to other designated applications. Most people are familiar with SSO through Google, since signing in to one Google property such as YouTube grants you access to Gmail and other applications. SSO is popular for companies with multiple brands since it allows for greater user visibility, as well as reduced friction. There are also use cases for SSO in workforce and B2B identity management.
User management and access control
One essential element to any IAM system is the ability to control who is permitted to access data by provisioning users with different roles. IDaaS systems simplify this process by centralizing identity and putting these controls into a single location like a user dashboard. That’s a significant advantage in making sure sensitive data stays in the right hands since it’s much less prone to error than an IT team manually controlling access to individual applications.
Why Enterprises Choose IDaaS
IDaaS is undergoing a period of exponential growth as more companies—from startups to multinational corporations—decide to outsource identity. The IDaaS market is predicted to grow from $2.5 billion in 2019 to $6.5 billion in 2024.
Why this shift toward third-party identity solutions? The reasons include the need to meet legal requirements, manage security risks, and implement an identity solution designed around scalability and extensibility.
Data privacy law compliance
One of the reasons that IDaaS has become so important recently is the rush to comply with new data privacy regulations. These include the EU’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and others.
Organizations that fail to comply with these regulations can face stiff penalties. For instance, under GDPR, organizations without secure and transparent data practices can be fined up to 20 million euros or 4% of annual global turnover — whichever is higher.
Data privacy laws often grant users more rights over their data. These rights vary depending on the law, but they may include:
- A new right to data portability
- An extended right to be forgotten (also called the right to erasure)
- The right to opt in or out of data collection and sales
These rights translate to a new set of obligations for organizations. It’s now essential to have a centralized repository of user data to satisfy reporting requirements and protect sensitive data according to current best practices. Data privacy laws are rapidly evolving, and managing compliance can be a full-time job, especially for organizations with uses in multiple jurisdictions.
Managing compliance is a major undertaking for any company. However, relying on an IDaaS partner can keep track of even siloed identity stores. A centralized identity solution can deliver lower maintenance costs and greater peace of mind. Although an IDaaS provider can’t ensure your organization will be fully compliant, IDaaS tools can certainly help.
Increased security With IDaaS
In recent years, identity has become a major source of high-profile hacks and data breaches. In fact, Verizon’s 2020 data breach report found that over 80% of breaches from hacking involved brute force attacks or the use of lost or stolen credentials.
The best protection against broken authentication attacks like credential stuffing are the features IDaaS providers specialize in: MFA, brute force and anomaly detection, and rigorous access control.
Extensibility, adaptability, scalability
Legal and security concerns are the most frequently mentioned benefits of partnering with an IDaaS provider, but a sophisticated approach to identity can also help growing companies boost their bottom lines. Organizations with custom-built IAM solutions frequently find that maintaining these systems and adapting them to new needs and partners takes months of developer time.
For instance, in 2019, Apple mandated that every app on the App Store had to include “Sign in with Apple” as a login option. Companies with bespoke IAM systems scrambled to meet this requirement, and many found that their systems were rigid and full of legacy code. Most IDaaS providers, on the other hand, included this as a simple update.
Having an extensible identity platform is also essential to integrating users during Merger and Acquisition (M&A) deals and in deals between enterprises. Two organizations with IAM systems that can’t talk to one another can’t benefit from each other’s data, but an IDaaS provider can act as a translator between different back ends.
What’s Ahead For IDaaS
IDaaS is an increasingly important segment of SaaS, propelled by new regulations, heightened security risks, and excitement about new technology.
Even organizations that typically adopt a "Do it yourself" (DIY) attitude about building their own features are beginning to recognize the value of relying on third-party identity providers. They can make that switch at any stage: during initial product development, prior to release, or at an inflection point at which they see the limits of their in-house IAM system.
The definition of IDaaS will continue to evolve as providers add new features, but the need for specialized expertise to handle these matters will remain constant.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.