Ideally, your new service or app is easy to use and access, and customers—who you want using your product as quickly as possible — can start using it with minimal friction.
Your core value proposition is just on the other side of a login screen, and making that entrance even marginally more difficult can risk sending those potential customers elsewhere.
Step-up authentication is a way to strike a balance between security and friction. It ensures users can access some resources with one set of credentials but will prompt them for more credentials when they request access to sensitive resources.
We'll go over three emblematic use cases for step-up authentication:
- Users want seamless access to certain resources, but organizations want to verify their identities before they access anything more sensitive.
- Employees need access to data to complete everyday work, but occasionally need access to private data that would cause damage if exposed.
- You have or want to deploy a membership model that limits complete access to your site or service to paying users.
Step-up authentication enables you to provide easy access to one layer of resources and secure access to another layer of resources. This makes authentication work for you and your users and unlocks new ways to run your business.
"Learn about the different use cases for which step-up authentication is essential to deliver a secure and frictionless user experience."
Tweet This
What Is Step-Up Authentication?
The goal of step-up authentication is to adapt identity requests to the importance of the resource and the risk level if it were to be exposed. Asking for too little gives your users (or whoever might be posing as them) a dangerous amount of freedom, whereas asking too much, especially up front, creates obtrusive friction.
You can't assume every user that offers a matching username and password is actually who they claim to be. Identity theft is a growing problem —for people and the businesses they use. Identity thieves can send phishing emails to steal credentials from unsuspecting users or pose as authority figures and request credentials or access. If users repeat passwords across services, a separate breach might leave their credentials—and your resources — exposed and up for sale for the low price of $50.
The fear this threat inspires causes some businesses to barrage users with security steps, but the best security is simple. Simple security keeps users happy and businesses safe. This is hard to implement on your own, but it’s easy when you have identity as a service.
The risk with step-up authentication is in the implementation. Target made itself vulnerable in 2013 by giving too many people access to data that they didn’t need. Though most employees couldn’t access sensitive data without two-factor authentication, Target let some vendors maintain access to their networks without it. Once the hackers controlled vendor credentials, they could then access Target’s point-of-sale system, eventually stealing 40 million credit cards.
Effective step-up authentication requires careful planning about who has access and who you ask to step up.
Step-Up Authentication vs. Multi-Factor Authentication vs. Adaptive Authentication
Step-up authentication is frequently in the same conversation as multi-factor authentication (MFA) and adaptive authentication, but there are important differences.
Step-up authentication and adaptive authentication are authentication systems, whereas MFA is a term that covers authentication factors both systems use.
MFA refers to authentication methods that go beyond username and password, such as biometrics, physical cards, and emailed links. You might require all users to submit multiple factors of authentication, or only some if you’re using adaptive or step-up authentication.
Adaptive authentication, also known as risk-based authentication, is similar to step-up authentication but is dynamic instead of static. Adaptive authentication systems automatically trigger additional authentication factors, usually via MFA factors, depending on a user's risk profile. A risk profile is determined by assessing:
- IP reputation: Is someone attempting to login from an IP address associated with previous dubious requests?
- Impossible travel: Frequency of requests from different geo-locations
- Known device: Whether the device is recognized or not
Risk profiles can also be informed by user role, resource sensitivity, and other variables. Adaptive authentication systems then prompt credentials that should be appropriate to the risk level of a request and its source.
With Auth0's Adaptive MFA, users are prompted for a secondary factor only when the primary factor login appears unusual or suspicious based on the three risk dimensions mentioned above — in other words when the login appears high-risk. For instance, a login request from a new device or an unfamiliar geo-location suggests that the login attempt may be fraudulent and that the user should be asked to authenticate with a second factor.
Step-up authentication is generally static and is based on predefined risk levels of resources and users. It focuses on the sensitivity and value of different resources, limiting them to users who can provide credentials that prove their claims for access.
When Should You Use Step-Up Authentication?
Any resource or data exposure can create a vulnerability, so effective use of step-up authentication requires care. It's generally best to keep all resources as secure as possible, but there are a few cases where it's useful to give many users some access, and some users more access.
Users need access to high-risk resources
In many cases, users don’t always need access to high-risk resources, but when they do, step-up authentication can make sure they are who they say they are.
For instance, mobile apps for banks often allow customers to make small changes and access limited information with only minor authentication. If customers want to check their balances or scan and deposit checks, the risk level is relatively low and the bank can let them proceed with only usernames and passwords.
If customers check their balances and decide to move funds around, the bank can then prompt them for more credentials if the moved money exceeds a certain amount. A one-time code, sent to a phone number or email address, can verify the identity behind the request.
While a security measure like that might annoy customers if they just want to see if their paycheck came through that week, they’ll likely be more patient authenticating an action known to be riskier.
Organizations often encounter similar use cases for their employees. For example, if your company has a GitHub Enterprise Server instance, you might want to enable your employees to easily review code and create new branches but limit them from committing code or changing repository settings.
This way, organizations can control who has the authority to commit code to production, which protects them from employee mistakes and bad actors posing as employees.
Users want to interact with sensitive data
With step-up authentication, employees can access the data they need every day without automatically getting access to sensitive resources. Once they do need access, step-up authentication can verify them as necessary.
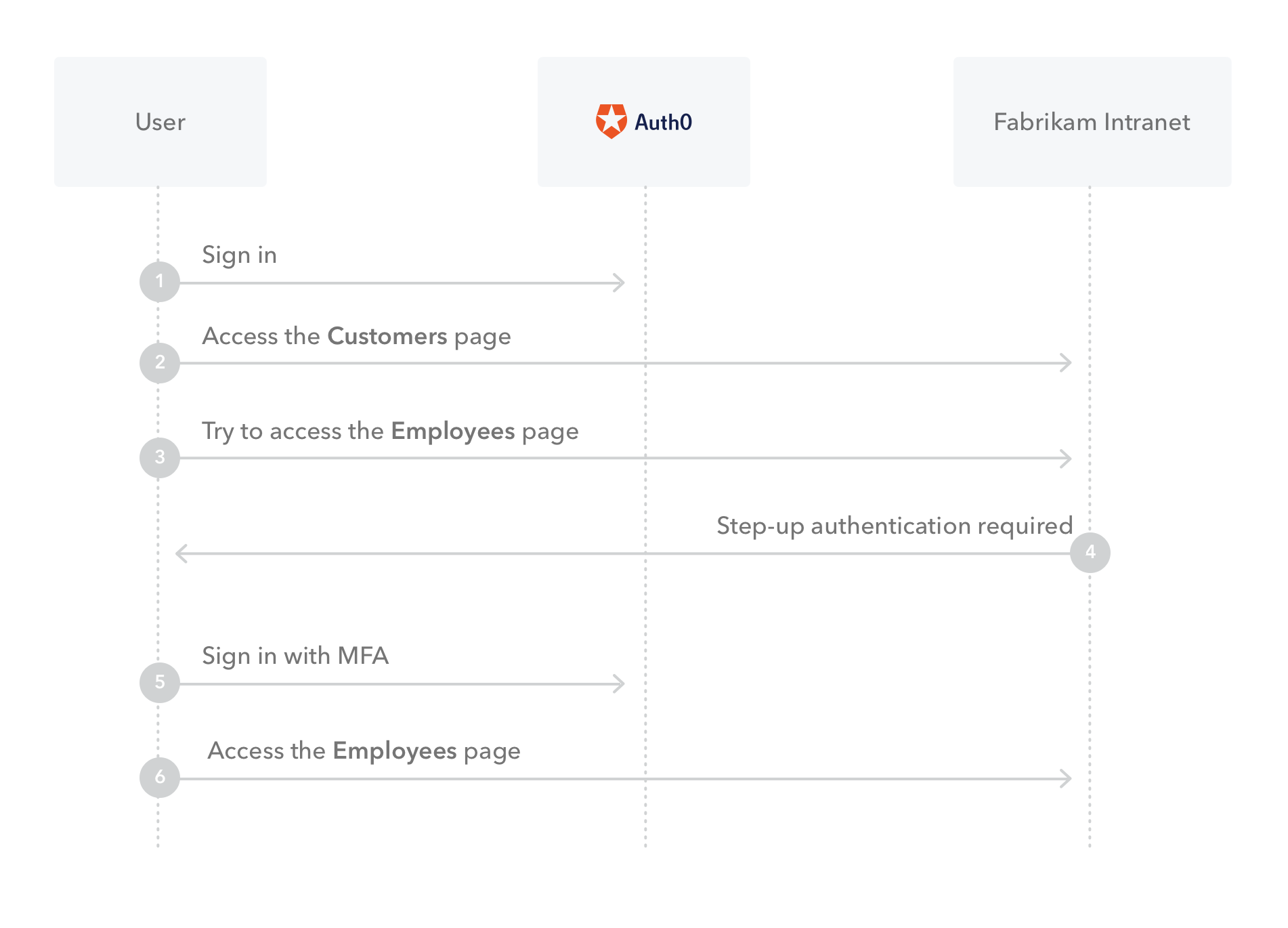
For instance, a company’s intranet service might enable streamlined access to limited subsets of customer information. That same service might also connect to more sensitive resources, such as salary data about fellow employees or private payment information from customers.
Below, you can see how Auth0 would prompt step-up authentication as users from Fabrikam, a fictional corporation, access the Intranet.
Even if a phishing campaign or data breach gave identity thieves your employee’s credentials, step-up authentication would block them from accessing sensitive data.
Businesses want to Privilege access for paying users
If you keep up with the news online, you’ve likely encountered a step-up authentication prompt. Major publishers like The New York Times and The Washington Post allow anyone to read articles from their sites—up to a certain point.
After reading a number of articles set by the site, a pop-up prompts you to log in to or create a paying account.
In this use case, step-up authentication encourages distribution and incentivizes new readers to pay for further access. When an article goes viral on Twitter, it can attract new readers who might enjoy the article and convince more experienced readers to pay so they can stay informed.
"What is step-up authentication and when should you use it? Find out in this blog post."
Tweet This
How to Implement Step-Up Authentication
Identity management looks simple, but the consequences of getting it wrong are dire. Data breaches can damage businesses, hurt reputations, and expose the private information of the very users you’re trying to serve.
Outsourcing identity enables you to keep working on your core service and implement authentication protocols and systems as necessary.
Auth0 makes it easy to add step-up authentication with extensible MFA support. With Auth0, your app or site can verify whether a user has already logged in via your selected MFA factors, and prompt a credential request if they haven't.
By setting policies with Auth0 rules, you can customize which MFA factors are necessary for different contexts and for different users. You can do this with application programming interfaces (APIs) or web apps.
If a user wants to transfer money with a bank’s app, for instance, and the app includes Auth0 step-up authentication, the app will send an access token that includes different permissions, such as the ability to view account balance or transfer funds. If the request doesn’t have the second parameter, the API redirects the user to Auth0, which prompts the user to enter more credentials. Once the user verifies their identity via MFA, the token will receive that parameter and the user will have access.
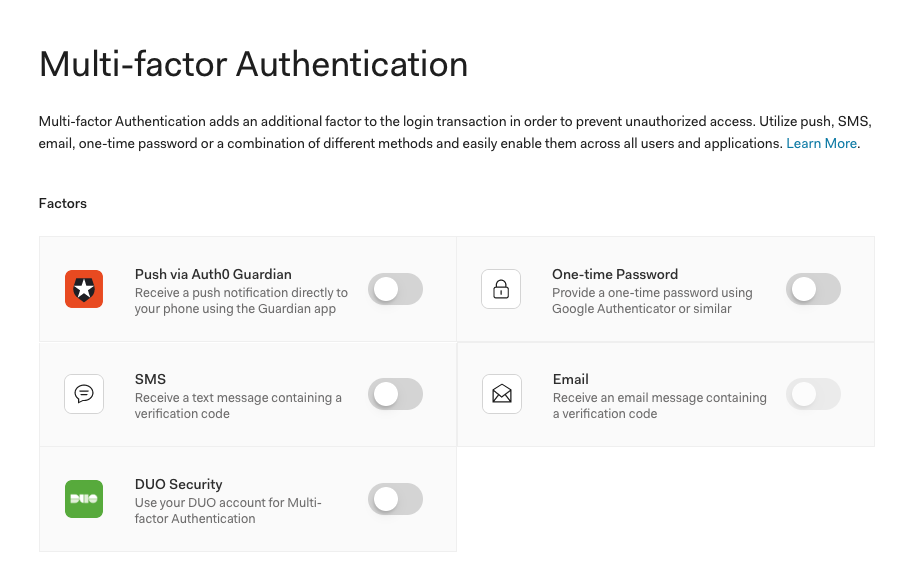
If you’re designing a web app, you can configure it so that when users go from one view to another, the web app prompts MFA. When users log in, a JSON web token will indicate their allowed access levels. If the MFA parameter isn’t present, Auth0 can redirect users and prompt them to input more authentication factors. It can be as simple as third-party authenticator like DUO, email, SMS, or with Guardian — push notifications.
Step up Security with Step-Up Authentication
Authentication doesn't have to feel like a barrier — you can adapt it, without sacrificing security, to the needs of usability.
Separating users with step-up authentication gives customers and employees the ability to complete minor tasks easily and access more important data smoothly. If you want to implement a membership or subscription model, step-up authentication can provide access privileges exclusively to paying users.
With an outsourced identity provider like Auth0, implementing advanced authentication methods like step-up authentication and MFA is simple. Auth0’s extensible tools give you the freedom to make authentication work for you and your users.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.