On October 30th, Apple released three new pieces of hardware. The MacBook Air, iPad Pro, and Mac mini come hot on the heels of Apple's iOS 12 rollout in September, along with additional changes to the iPhone and Apple Watch.
Far more than just expensive stocking stuffers, these devices have important security features that Mac-using teams should be up to date on. For teams looking to modernize their legacy systems, endorsing device upgrades is a concrete first step.
While many companies, particularly in finance, still rely on PCs, several tech-forward teams like IBM and SAP have brought Macs into the workplace. With many more employees working remotely and from their personal devices, it's important for all companies to stay up to date on these new devices — and their security features.
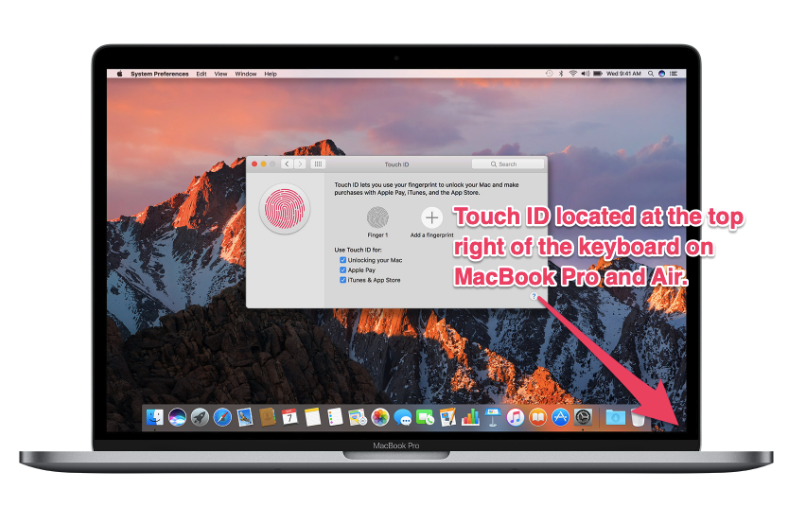
The new MacBook Air includes Touch ID.
In gold, silver, and space gray, the new MacBook Air finally has a fresh design for the first time since 2015. Its screen (13.3 inches) stretches across almost the entire width and has four times as many pixels (4 million total) as the prior version, which makes for a far more immersive visual experience. It also has an improved keyboard, which is quieter than the 2015 version and has a larger trackpad.
In addition to the new retina display, the 2018 MacBook Air incorporates Touch ID that allows users to log on and make payments more securely.
Touch ID is a form of biometric authentication, which requires inputting a unique physical feature (e.g., a thumbprint) to move forward.
[Source: Apple]
Biometrics used elsewhere include voice recognition, typing recognition, and even gait analysis.
Touch ID isn't a new feature (many users use it on their iPhones); however, it's new to the MacBook Air and improves the speed and quality of the experience.
Touch ID on the MacBook Air has several advantages. Primarily, if someone steals your device, and you've set up Touch ID, they won't be able to access your files without your fingerprint. Even if they have figured out your password, they won't be able to break in. As with other multi-factor authentication methods, sealing sensitive data with additional layers of proprietary information can divert hackers towards easier targets.
One disadvantage of Touch ID is that Apple learns a user's fingerprint, based on a series of initial images it takes, which leaves room for error. A sensor combines several sections of a fingerprint and categorizes them into one of three basic fingerprint types: the arch, the loop, or the whorl. According to Apple, this mathematical representation leaves a 1 in 50,000 chance that two people will be able to log into the same device to make the same transaction. To mitigate the risk, Touch ID improves its matching accuracy over time, based on a larger sample of log-in attempts.
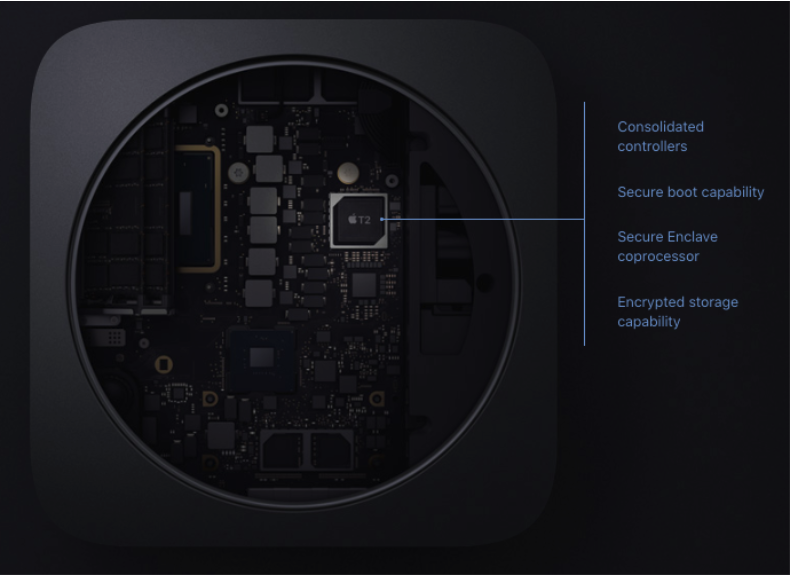
Touch ID runs on Apple's new T2 chip. The T2 is a secure co-processor that works alongside the main CPU — the part of a computer that receives inputs and runs programs. The T2 (an update on the 2016 T1) focuses largely on encryption-related operations, underlying Touch ID. Because it exists separately from the CPU, the T2 diverts sensitive data from the core processor, which is what hackers often aim for.
For teams working with sensitive customer information, T2 and Touch ID work in unison to create a safer workflow.
The iPad Pro relies on deeper machine learning with new Face ID feature.
[Source: Apple]
The iPad Pro offers many advantages for teams and individuals on the go. It's highly portable — 25% less volume and just 5.9 mm thin— yet maintains the largest display of any iPad. Its screen adjusts to the viewer's orientation (e.g., if you flip it lengthwise, like the iPhone, the display will flip accordingly), and Apple's True Tone and anti-reflective coating makes the experience feel more natural, particularly after heavy usage.
The iPad Pro also incorporates Face ID — another form of biometric authentication. As you might guess, Face ID relies on the user's facial features to unlock the device, which many see as a step beyond a simple thumbprint.
To achieve this level of recognition, Apple has embedded a deeper level of machine learning into the new iPad Pro. Its TrueDepth camera creates a detailed map of a user’s face from 30,000 data points. From there, the Secure Enclave (part of the T2 processor) encrypts it. The more times a user logs in, the more the software refines the facial model. It starts to learn a user's face even if she or he is wearing a hat or sunglasses, grows a beard, or puts on makeup. If it detects a close match (but not close enough), it prompts a user to enter a password for confirmation.
Because the iPad Pro is easy to travel with, the added facial recognition element helps balance the risk of taking sensitive data outside of an office environment.
Mac mini helps secure the home office.
Many people don't think of adding an extra layer of security when working from home; however, with the number of data breaches on the rise, being as careful as possible can pay off.
Suitable for both home computing and industrial-size tasks, the Mac mini has finally emerged from its prior 2015 form. The device has five times the speed of the old version and 70% more MSP (maximum sustained power) for working with larger files.
Many people use Mac minis at home if they're doing tasks like creating and uploading videos and music. Because it's not tied to a specific screen, the computer is more versatile, as well. It can easily sit on a desk or in a corner — wherever it's more convenient.
With regards to security, the Mac mini also relies on Apple's T2 chip.
[Source: Apple]
T2 also supports Secure Boot, which helps ensure that when you start the computer, it loads only trusted software. If the OS doesn't pass verification, the user will be prompted to reinstall the software — or select a different startup disk, which will also have to pass inspection.
Running software that is outdated can introduce enormous risks into your system — holes that cybercriminals can move through or even the simple danger of losing data on your own if the computer shuts off or doesn't save work properly.
The Mac mini isn't as high profile as the rest of Apple's hardware, but for the employee without the benefits of traditional workplace security, it's a great foundation for keeping safe at home.
Modernize your legacy systems to stay safe and productive.
Updating your legacy systems, even at the level of individual pieces of hardware, can have an enormous impact on your workflow and security. New Mac products are expensive (the 2018 MacBook Air starts at $1,199, and the iPad Pro and Mac mini start at $799), but the benefits of safer authentication, separation between the core process and T2 chip for encrypted data, and the ability to double-check your OS before you run it can be profound.
Running on the latest systems can help mitigate threats like spyware, phishing, and bucket brigade attacks, also known as man-in-the-middle (MITM) attacks, which have nearly destroyed companies.
Even if your company hasn't invested in Mac devices, with many employees bringing their own devices to work these days or working remotely, understanding the rewards and vulnerabilities of the new Mac products can help you make smarter security decisions for your team as a whole.