How long should a customer stay logged in to an application? The Open Web Application Security Project (OWASP) and the National Institute of Standards and Technology (NIST) state that it's safer for customers to sign in to your app for mere minutes. Limiting your customers to hold short sessions may leave them frustrated and unwilling to come back to use your application. A pillar of customer retention is to provide both a user-friendly and secure user experience. However, balancing those two user experience components is a real challenge for most businesses.
OWASP recommends application builders to implement short idle time outs (2-5 minutes) for applications that handle high-risk data, like financial information. It considers that longer idle time outs (15-30 minutes) are acceptable for low-risk applications.
On the other hand, NIST recommends that application builders make their users re-authenticate every 12 hours and terminate sessions after 30 minutes of inactivity. For intermittent re-authentication, that session termination time shrinks to 2 minutes.
These guidelines by OWASP and NIST provide an ideal foundation to implement session security in applications. However, before you choose to extend your application's session length, it's also ideal for your team and your internal stakeholders to discuss how such a decision can impact your application's user experience.
Ultimately, balancing security and user experience is key to achieve customer retention. A tedious authentication process can exhaust your customers and discourage them from using your application. A seamless, perhaps even invisible, authentication process can instead encourage your users to spend more time with your application securely.
Auth0 offers you a feature called long-lived sessions to offset the cost of implementing a secure user experience around authentication.
"UX can help you keep or lose a customer. Balance #UX and #security with Auth0 long-lived sessions."
Tweet This
Why Customers (And Businesses) Want Long-Lived Sessions
One of the conveniences of email services like Gmail is that you can check your email sporadically without having to face repetitive login prompts. Imagine how tedious it would be if you had to log in every time that you go idle for more than two minutes.
For media companies, like Alma Media, customers may visit their site infrequently. Registered users often visit media sites every two weeks to consume content. Returning users who face the hassle of signing back in may opt to stop visiting the site. For a media company, losing its audience means losing ad revenue, since clicks generate payments on ads. If the revenue strategy also involves targeted advertising, media companies require a security strategy that favors maximum engagement with minimal friction.
If a company offers an essential service, its users may not have the option to leave the site. However, they may still become vocal about their dissatisfaction with the user experience on social media or review channels.
For example, a utility company may have monthly or quarterly billing cycles where end-users access its application to pay their bills. Other companies like Autotrader have customers with usage patterns that vary widely based on purchase and maintenance cycles. For any application with long periods between end-user engagement, users understandably forget their passwords.
Some Auth0 customers have reported that as much as 22% of their customers forget their passwords each quarter. Frustrated customers have to contact call center staff to request password resets. Forgotten passwords may lead to decreased customer satisfaction, paired with increased business operation costs.
For low-risk engagements, you can provide better user experience by implementing a longer session limit, which could become the difference between keeping or losing a customer. While Auth0 focuses on making your applications more secure, we also understand the substantial value of your end-user experience.
Everything considered, long-lived sessions work exceptionally well for organizations with periodic or even intermittent engagement cycles.
Poor user experience can lead to customer dissatisfaction. Insufficient security can amount to legal penalties, fines, and losing customer trust. The combination of poor user experience and insufficient security can compound into a catastrophic punch to damage a brand.
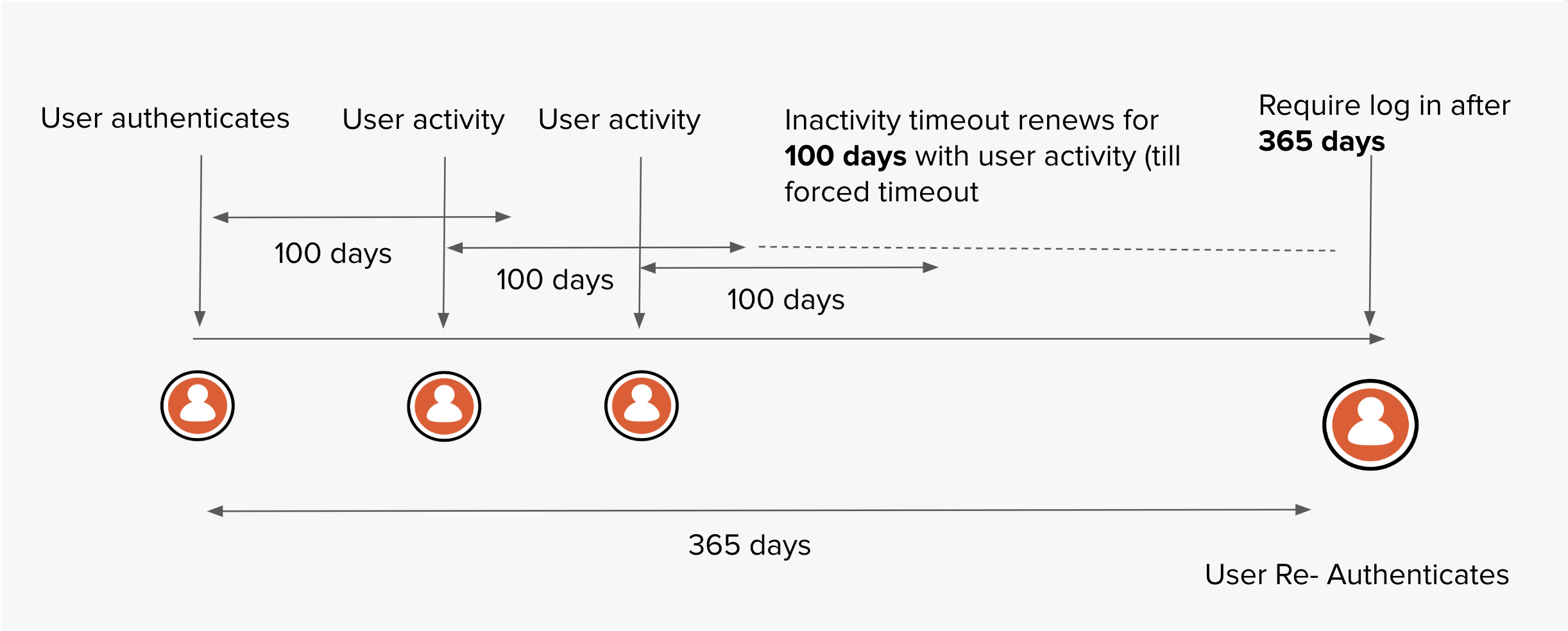
100 Days Inactivity/365 Days Total Timeout
Auth0 lets you customize session lengths to fit the security risk tolerance of your desired user experience. You can configure session limits with up to 100 days of inactivity (idle timeout) and up to one year in total duration (absolute timeout).
The motivation behind the 100-day idle timeout cap is to cover one quarter plus a few days, which provides wiggle room for people who log in to do end-of-quarter reports.
Long-lived sessions allow companies with quarterly, monthly, or other types of customer engagement cycles to reduce friction for end-users and provide secure access to low-risk content and functionality.
Whenever your customers need to perform high-risk actions, such as changing account details or updating payment methods, you can rely on Auth0 functionality to programmatically require password validation to run those actions as an added layer of security.
With Auth0's long-lived sessions, session management, and Single-Sign On (SSO), you can build a better user experience for returning customers, enable personalized targeting, and reduce the costs of operations by mitigating password resets. If you'd like to learn more about how you can customize Auth0's out-of-the-box features to fit your needs, please reach out to sales@auth0.com.